5 Dark Web Trends in 2023

2023 Dark Web Trends
The dark web is designed to anonymize web traffic. This simple concept is fundamentally important for maintaining truly private web surfing and communications. For journalists, intelligence agents, and everyday citizens living in oppressive regimes, the dark web is a critical tool for supporting free speech and open access to news. Unfortunately, this same benefit is also useful for criminals, who routinely leverage the dark web to peddle illegal or stolen goods, obtain malware or other malicious tools, and coordinate their nefarious activities.
Let’s look at how criminals are using the dark web in 2023 and identify dark web trends so that cybersecurity teams can hone our techniques and defend effectively.
1. Dark web activity is increasing. In 2023 the dark web has over 2.5 million daily visitors, and it’s estimated that more than half of those visitors have participated in illegal activities. What’s even more alarming is that in April 2023, daily dark web visitors rose by 200,000 to reach 2.7 million.
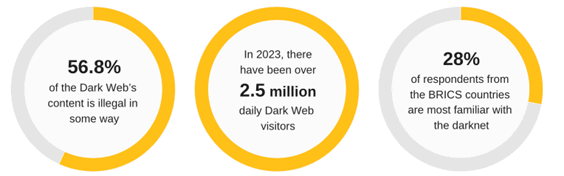
Source: https://www.banklesstimes.com/dark-web-statistics/
Why is dark web use increasing? There’s speculation that the increase in extortion exposure attacks is driving more journalists and organizations to the dark web to check extortion exposure sites, and the increasing number of malware-as-a-service option continues to enable criminals with limited programming skills to engage in cybercrime. The anonymity of the dark web is also a big benefit for whistleblowers submitting sensitive information to news outlets. Some mainstream publications such as the New York Times maintain a presence on the dark web for just such tips, and other publications around the world maintain a presence to circumvent government-imposed internet censorship. For example, during the Russian-Ukraine conflict, citizens used dark web versions of social media to share information when traditional access was blocked.
The increased use of the dark web is also a boon to cyber extortionists, who feed off traffic to their data leak portals and work to build relationships with the mainstream media. It’s clear that criminal activity on the dark web continues to grow and thrive. So, the takeaway is that you should continue to strengthen your security posture to defend against potential attacks.
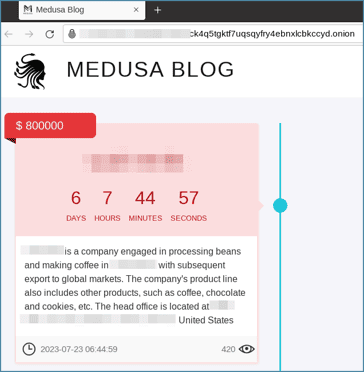
Here’s an image from the Medusa blog showing the countdown for ransom payment before stolen data is released.
2. More dark web sites are offering freebies. One of this year’s dark web trends is oddly collaborative. Usually, criminals sell access to exploits and stolen data, but increasingly sites such as 0day.today are releasing more free material, from exploits to data dumps. For example, take a look at the 0day.today web site screen shots below. This is a popular dark web site that peddles software exploits which hackers can use to break into your computer or network. In 2022, the site was focused on getting visitors to BUY exploits, while in 2023 it emphasizes that “Most of the material is completely FREE.” It’s too soon to tell whether this is a short-term marketing tactic or a lasting dark web trend.
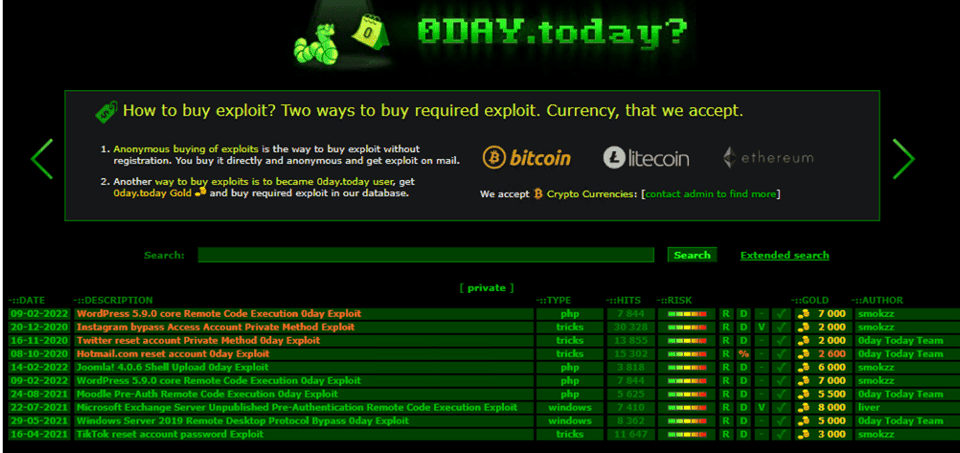
2022 screen shot from 0day.today that emphasized buying information.
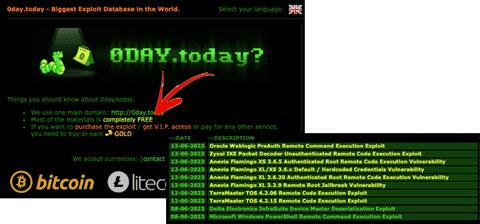
2023 screen shot from 0day.today emphasizing most of the information is free.
3. Law enforcement crackdowns targeting the dark web have increased and generated substantial wins in the last year. Starting with the Joint Criminal Opioid and Darknet Enforcement Team (JCODE) creation in 2018, coordinated international law enforcement initiatives have increased and ultimately led to some big wins in the past year. In May 2023 the Justice Department announced the success of Operation SecTor, “a coordinated international effort spanning three continents to disrupt fentanyl and opioid trafficking on the darknet, or dark web.” In 2023 they took down the Hive hacking group in January, dismantled the Genesis dark web marketplace and arrested 120 suspects in the spring, and busted EncroChat’s mobile criminal forum in early summer.
Much of this progress can be credited to sophisticated techniques that investigators now use to trace cryptocurrency wallets and mixers, so that payments exchanged in dark web markets and other criminal enterprises can, in some cases, be effectively traced. . For example, two months ago a Russian national was arrested in Arizona for allegedly deployed LockBit, Babuk, and Hive ransomware. Law enforcement was able to track him through cryptocurrency transfers to wallets that were linked to his name, then forensics law enforcement was able to link those transfers to his verified identity for his Bitcoin wallet and capture him. The increased law enforcement activities of the past year are changing the landscape of cybercrime—one of the dark web trends about which we can all be happy. However, criminals continue to adapt.
4. Security is increasing on the dark web. Likely a response to increase law enforcement activities, it is even harder to get access to dark web hacker forums. Dark web forum admins have always been wary of newcomers and visitors, routinely screening for law enforcement (often ineffectively). In light of recent busts, however, dark web operators have increased their vigilance and are scrutinizing applicants more thoroughly. These days, you often have to pass stringent verification and vetting processes to join a forum. Admins may require references from other members or verification tokens from other trusted forums. Some forums and dark web marketplaces now require a substantial cryptocurrency down payment to even get access to their services. In the face of increasing law enforcement activities, cyber criminals are increasing their security accordingly rather than exiting the cybercrime business.
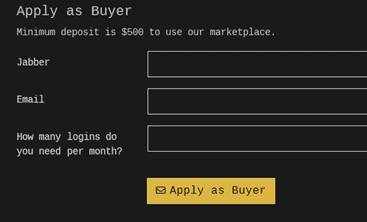
Here is a screen shot of a minimum deposit requirement to join a dark web marketplace.
5. Rating services are increasingly popular since dark web marketplace “exit scams” remain high. There is no honor among thieves in many corners of today’s dark web. “Exit scams” occur when marketplace operators suddenly shut down, stealing funds from escrow wallets and disappearing. When this happens, buyers and sellers are out of luck. Dark web visitors have turned to sites like Dread, which is similar to a dark web version of Reddit, for information. You can use Dread to learn which dark net markets are reputable and their locations. On a recent visit to Dread, we discovered that the ViceCity dark web market was in the middle of an exit scam. At the same time, the Abacus market, which provides everything from guns and drugs to stolen data, forged documents, and hacker services, had almost perfect customer reviews for its criminal marketplace. Dread offers feedback percentages and ratings like many clear web sites vendors. This enables dark net vendors to develop their reputation among criminals.

Screen shot from Dread dark web forum advising users of ViceCity exit scam.
What to do if your information is found on the dark web
We’re often asked if dark web scanning is effective. Sadly, the answer is no—it’s not possible to scan the entire dark web. While some companies do offer this service, be aware the results are always incomplete, because there are many private forums and sites that simply cannot be discovered or indexed by a scanner.
That said, scanning services typically comb through data available on many places in the dark web, and while the results may not be complete, they can be useful. Dark web scanning may help with historic breach information, but it likely won’t help you identify if you were part of a recent breach (you can also check for free at public sites like https://haveibeenpwned.com/). Here’s what you can you do if your information is found on the dark web?
1. Don’t Panic!
2. Change your passwords and create unique, strong replacements. Organizations and individuals should use a password manager to suggest and store passwords to reduce password reuse (which increases attacker access in a credential hacking attack).
3. Enable strong MFA whenever possible. Read our MFA tip sheet for more details.
4. Watch out for phishing, smishing, and vishing attempts. Once your information is out there, you will likely experience more frequent social engineering attacks and these attacks will likely include more personalized information. Organizations should conduct regular cybersecurity awareness training that includes mobile security and phishing simulation tests. Also, criminals are increasingly using databases of stolen employee mobile phone numbers to attack employer networks. Read our blog on mobile security best practices for details.
5. If your personal information is stolen, monitor your credit report for unauthorized activity or accounts. You can also freeze your credit report for a year after you have been a victim of a data breach. This ensures credit reporting agencies will not provide your credit report if anyone tries to open a new loan or credit card account in your name.
6. Add additional challenges for financial accounts and mobile providers wherever possible. Add additional authentication steps, enable challenge questions, and lock any access or privileges you don’t need.
We hope you found this information about dark web trends helpful! Please contact us if your organization needs assistance strengthening your cybersecurity posture.
