The Beginner’s Guide to the NIST Cybersecurity Framework & Password Guidelines

One of the best ways your organization can enhance security and combat constantly evolving cyberattacks is to leverage the NIST cybersecurity framework. The NIST cybersecurity framework provides a structured and organized process that helps you to evaluate your security program and prioritize the next steps to enhance your cybersecurity posture. To help you get started, we’ll give you an overview of the framework and how to use it.
To begin, NIST stands for the National Institute of Standards and Technology. It is a non-regulatory agency that was founded in 1901 and is now part of the U.S. Department of Commerce. NIST provides, and regularly updates, the standards, technology, and measurements that are used in virtually any electronic device or instrument you can imagine.
The NIST cybersecurity framework is a voluntary, helpful tool to assess and reduce cybersecurity risks. By leveraging the NIST cybersecurity framework, you can ensure that your organization meets the baseline cybersecurity guidance, and structure an ongoing plan to gradually increase your cybersecurity maturity (for more details read this blog on planning NIST CSF security gains). The NIST cybersecurity framework has many complexities, but this is a quick, high-level overview for those new to the framework. It also includes an overview of NIST password guidelines, as these guidelines are easy for any organization to implement and are a quick way to improve cybersecurity.
What is the NIST Risk Management Framework?
NIST is considered an industry standard baseline when it comes to certain guidelines such as the NIST Risk Management framework, NIST Cybersecurity framework, as well as guidance on password requirements, strong authentication, incident response preparedness, business continuity planning, and many other technical and process aspects of cybersecurity. The NIST risk management framework is a repeatable process that organizations can follow to identify cybersecurity risk, reduce risk to an acceptable level, and monitor risk over time to adapt to changes.
As cybersecurity risks evolve, so do the NIST standards. In February of 2022, NIST also published a ransomware risk management framework that can help organizations structure their ransomware response plans. In April of 2022, NIST completed its public input period that will inform their next set of NIST cybersecurity framework updates that will address today’s threats, incorporate supply chain security recommendations, and provide potential updates to the framework and tools. These frameworks are a free resource that can help organizations structure their cybersecurity and response plans. Read on for the high-level details so you can begin your plan!
The NIST Cybersecurity Framework Explained
The NIST Cybersecurity Framework is of particular importance. It is a comprehensive, enterprise-wide security controls framework that consists of industry standard best practices for managing cybersecurity risks. NIST guidelines can also be helpful for organizations implementing cybersecurity controls to support compliance requirements. It has three main components:
NIST Cybersecurity Framework Components
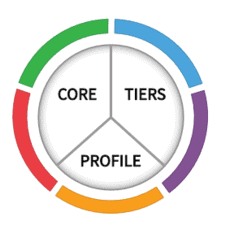
Image 1: This image is the property of the National Institute of Standards & Technology. Source link.
The Implementation Tiers
The four Implementation Tiers are Partial, Risk Informed, Repeatable, and Adaptive. They provide context on how an organization views cybersecurity risk and the processes in place to manage that risk. The tiers reflect a progression from reactive security programs to programs that are agile and risk-informed. Organizations can use the tiers to describe their current status as well as to set goals or targets for the organization to support planning and prioritization of cybersecurity initiatives and improvements.
NIST Cybersecurity Framework Implementation Tiers
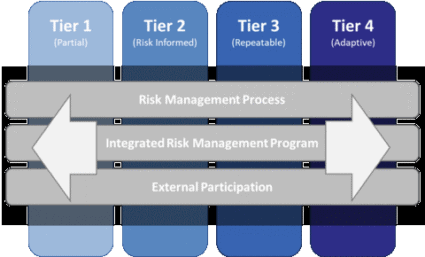
Image 2: This image is the property of the National Institute of Standards & Technology. Source link.
The Core
The Core of the NIST cybersecurity framework describes cybersecurity activities and desired outcomes in five core functions:
- Identify: Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
- Protect: Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services.
- Detect: Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event.
- Respond: Develop and implement the appropriate activities to take action regarding a detected cybersecurity event.
- Recover: Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event.
Each function is divided into categories to group related security activities. The categories are further divided into subcategories, which provide suggested activities that assist in achieving the desired outcome for the category.
NIST Cybersecurity Framework Functions & Categories Image
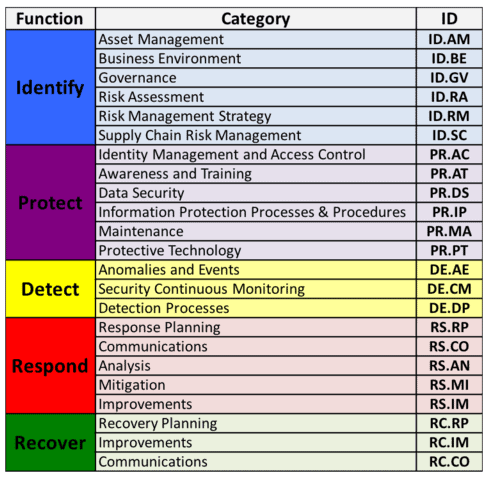
Image 3: This image is the property of the National Institute of Standards & Technology. Source link.
The Profile
The Profile component helps the organization produce a desired outcome based on their budget, risk appetite, and mission priorities, using information obtained through the Core and Implementation Tier components. One approach is for businesses to build a current cybersecurity profile of where they are in each of the five framework functions and categories, as well as a target profile of their cybersecurity target goals. This highlights the gaps and enables organizations to create a prioritized implementation roadmap based on their needs and budget. Most organizations create a multi-year, prioritized plan to reach their cybersecurity objectives. In LMG Security’s experience, identifying current and target tiers for each of the framework’s core functions can be a valuable communication tool within an organization if they are tracked and updated over time as the steps are taken to fill identified gaps and improve the security program.
NIST Password Guidelines
While the NIST cybersecurity framework covers a lot of important topics, passwords and strong authentication are of high importance for all organizations. The framework addresses passwords and authentication in the Protect function in the category called “Identity Management, Authentication and Access Control”. LMG Security recommends the following strategies for implementing and enforcing strong passwords.
- Passwords must not contain significant portions of the user’s account name, organization, or full name.
- Standard user passwords should be at least 16 characters.
- Administrator and service accounts should be at least 25 characters.
- Require minimal complexity rules to encourage longer passwords.
- Set a maximum password age to require passwords to be changed at specific intervals (i.e., one year).
To meet these requirements, LMG encourages users to think in terms of passphrases rather than passwords. An effective approach to creating passphrases is to use a full sentence or song lyric, using four or more words.
Where possible, implement technical mechanisms to enforce long strong passwords. Leverage a password manager solution to help users keep track of their passwords and reduce re-use of passwords across accounts. While your organization is thinking about passwords and authentication, you may also want to consider your privacy policies. Check out this blog on the NIST Privacy Framework that highlights some of the benefits it provides for managing privacy risk.
Getting Started
It’s clear that the NIST cybersecurity framework and guidelines are applicable to all organizations seeking to reduce cybersecurity risk and build a strong security program. Whether you tackle the whole framework or use it as a resource to address specific concerns, the framework can help you meet your organization’s cybersecurity needs. Even having a high-level understanding of the cybersecurity framework is a big first step in protecting your organization’s devices, information systems, and the valuable data that they are storing.
Contact us if you need help assessing your cybersecurity gaps and prioritizing your path forward. Our NIST CSF Guidance package ensures you have access to cybersecurity experts who take the burden off your team and help you develop a plan that fits your needs and budget.
To learn more about the NIST cybersecurity framework, visit https://www.nist.gov/cyberframework.
