A Dozen Mirai Botnet Easter Eggs—Revealing the Lighter Side of Malicious Code
 Working in Information Security, especially when hunting malicious hackers, can be stressful. Which is why it’s always a little exciting when we look at the malware source code and find unexpected Easter eggs (for the uninitiated, these are jokes left within the code). Given the time of year, we thought we would share one of our favorite examples, the Easter eggs we found within the Mirai botnet source code.
Working in Information Security, especially when hunting malicious hackers, can be stressful. Which is why it’s always a little exciting when we look at the malware source code and find unexpected Easter eggs (for the uninitiated, these are jokes left within the code). Given the time of year, we thought we would share one of our favorite examples, the Easter eggs we found within the Mirai botnet source code.
In reality, there is very little that is funny about the Mirai botnet malware. It has done a lot of damage over the years and took down much of the internet in the 2016 Dyn attack and is still widely used today. Despite its sinister reputation, we were surprised to find the Mirai source code was filled with quirky jokes. While this is a welcome break from code analysis, Easter eggs within a program are also a valuable source of information about the hacker (or hackers) that wrote the code.
What do Easter eggs in the source code tell you?
Besides letting you know that the hacker has a sense of humor, Easter eggs in the source code provide an interesting peek into the mind of the developer. Whether the developer placed the Easter eggs in the code to make themselves laugh or to make people reading it laugh, looking for Easter eggs in source code can tell you valuable information, such as:
- How long the author(s) worked on the code—more Easter eggs usually means more time spent developing the malware.
- How dangerous the code is—A larger number of Easter eggs can also provide a peek into the hacker’s intentions. When there is a larger emphasis on fun and games, it is usually not the most exploitative code and there may be more opportunities to get around it.
- How professional the hackers are—No Easter eggs in long, complex code increases the odds that the hackers are a professional team, sometimes working from an office, designing malware for maximum profitability .
Using these clues can help us see into the mindset of a hacker to crack the code and help plan a safe Mirai botnet containment and removal strategy.
Mirai Botnet Easter Eggs
Here are a dozen of our favorite Easter eggs (because all eggs should come in a dozen, right?). While these are not the only Easter eggs in the Mirai source code, we think these are some of the best. As you look at the code images, please note that everything with two slashes in front, and colored blue – // – are comments the author placed in the code.
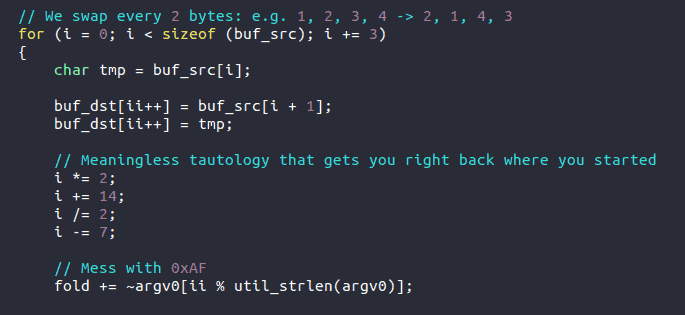
The first Easter egg is specifically for programmers. The author plays with the I variable and comments that it is meaningless repetition—something we all face from time to time.
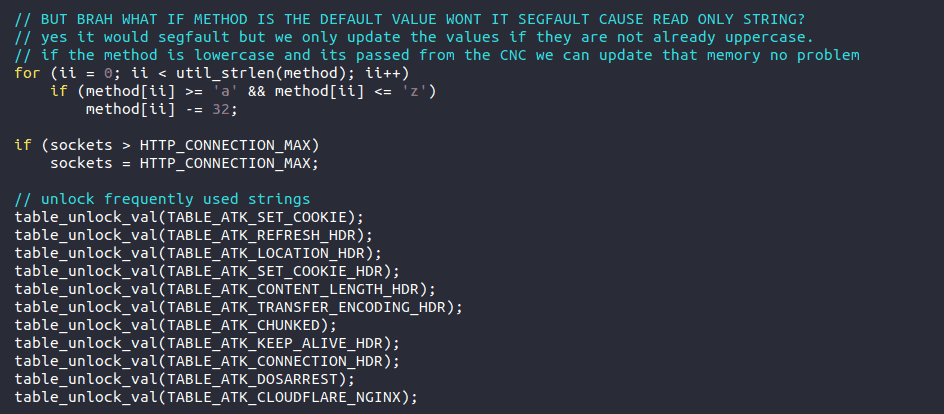
The second Easter egg shows that author’s playful side as s/he directly addresses the reader, asking and answering the question. Thanks, “Brah.”
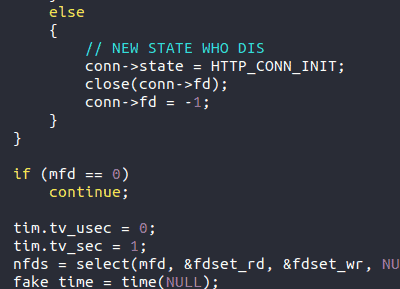
The third Easter egg is a play off the popular meme, “New phone, who dis.” I have to admit this one made us chuckle.
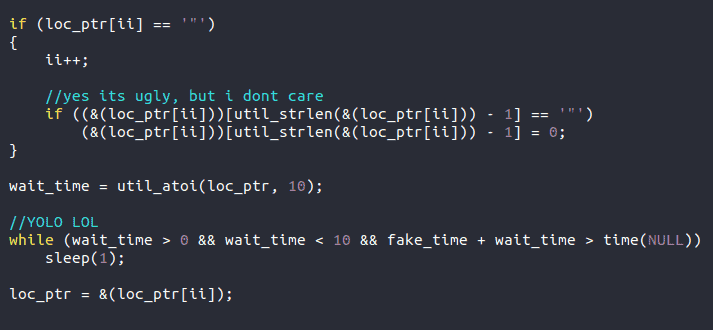
The fourth Easter egg seems to show the author getting a little bored…but you do only live once.
The fifth Easter egg comments about variables in the code.
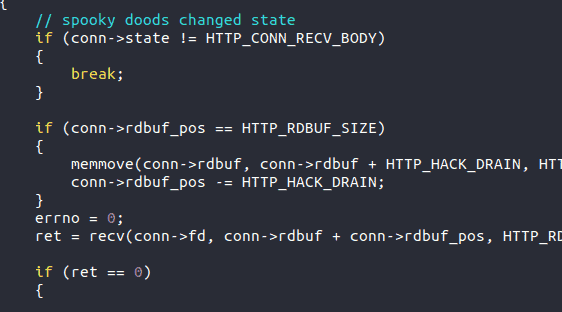
The sixth Easter egg features the author’s thoughts that these are easy hacks and jokes that if the local send buffer is full, so there is no need to rush (with a smiley face).
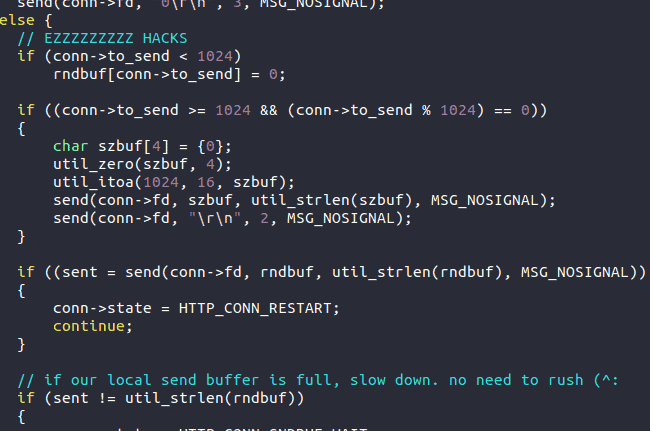
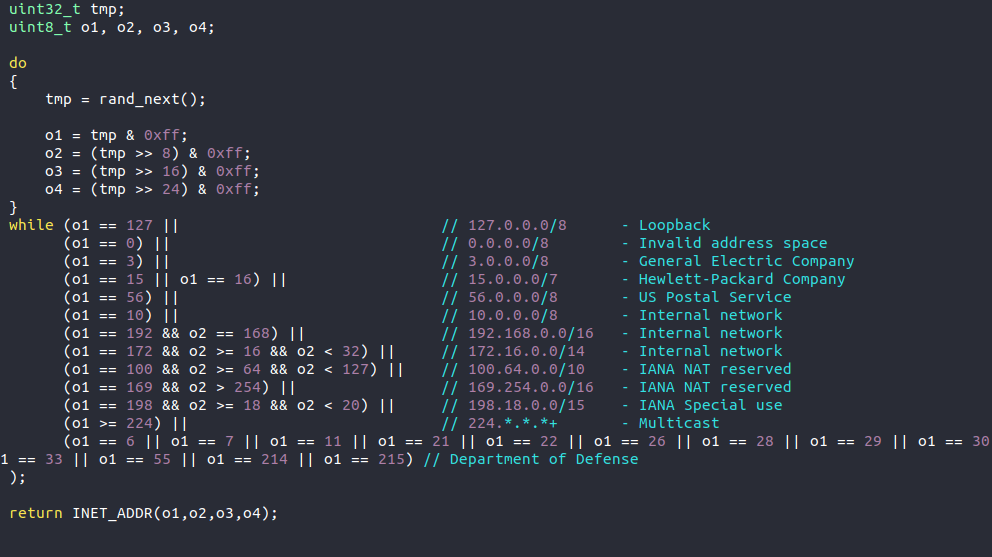
The seventh Easter egg offers valuable information—it shows that the author wants to avoid GE, HP, the DOD and the USPS. This gives us information on the scope and something to ponder.
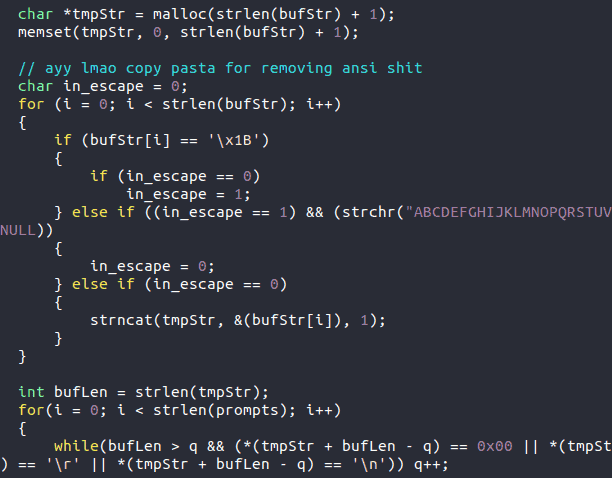
The eighth Easter egg shows the author poking fun at him/herself as s/he admit to using copy pasta (frequently copied and pasted segments in the code).
The ninth Easter egg shows an oddly introspective moment.
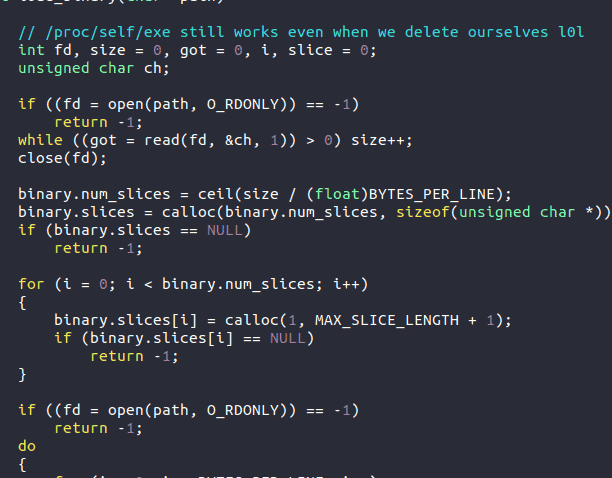
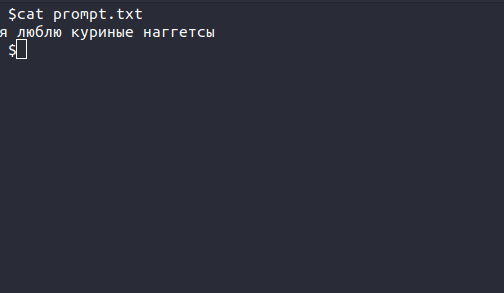
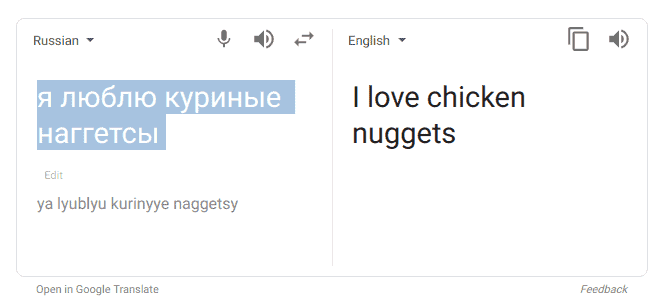
The tenth is my personal favorite. We found this in a text file within the user interface. It is in Russian, and you can see the translation below. Perhaps the author was getting hungry?
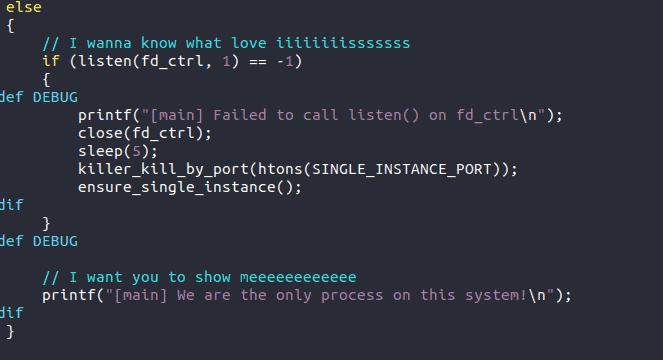
The eleventh Easter egg offers the lyrics to, “I Wanna Know What Love Is.” Apparently, sometimes hackers get lonely.
To complete our dozen, we’ll end with a safe string YouTube link to Rick Astley’s “Never Gonna Give You Up.”
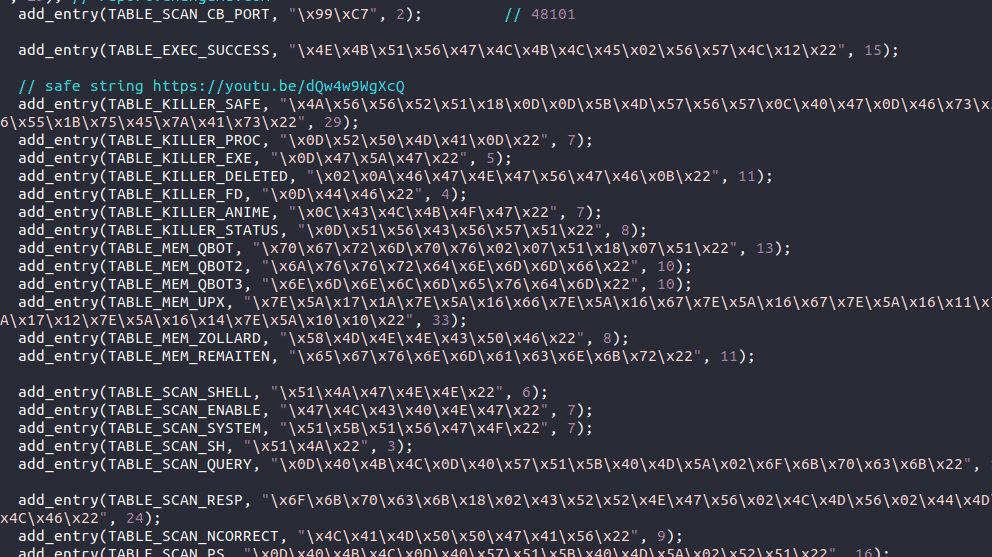
Well, now that we have all been Rick Rolled in the Mirai botnet source code, I think it’s time to wrap this up. We hope you enjoyed hearing the lighter side of LMG’s digital forensics experience and please contact us if you need any help with Mirai botnet containment and removal.

