After the Ransom was Paid: The Groundbreaking Events following the Colonial Pipeline Ransomware Attack

While the Colonial Pipeline ransomware attack may have been big news, what happened after the ransom was paid is even more fascinating. The Department of Justice recently recovered $2.3 million of the ransom that Colonial Pipeline paid to a hacker group (Darkside) responsible for this brutal cyberattack on American infrastructure. Ransom payments are rarely recovered, so let’s take a deeper look into this interesting case.
How Was the Ransom Recovered?
After the ransomware attack, Colonial Pipeline paid the cyber-criminals approximately 75 Bitcoin to relinquish control of the network and provide a decryption tool to unlock the files. This led to the US regaining control of the network infrastructure of the nation’s largest oil pipeline. As promised, the ransomware gang also delivered the decryption tool; however, the tool was poorly designed and inefficient, so Colonial Pipeline opted to restore the network with their own backup systems instead.
Meanwhile, the Department of Justice (DOJ) was monitoring the transaction and waiting for the ransom funds to land in a digital wallet. Once they had the wallet address, they were able to authorize a warrant and seize the majority of the ransom. The DOJ’s ability to follow a cyber ransom transaction sparks a significant turning point in the battle against ransomware. According to LMG’s incident response expert, Matt Durrin, “It shows a flaw in the ransom payment model. If the money is held in an exchange in the US, the US government can subpoena it.”
In light of this new ransom recovery success, will hackers be deterred? Or will we simply see them evolve their own ransomware attack strategy, perhaps moving to a more secure cryptocurrency such as Monero (XMR) or relocating escrow accounts to outside of the United States? We’ll share more of the ransom recovery details and what it means for hackers later in this blog.
The Criminals Aren’t Just in Hot Water with the US Justice System. They’ve Also Been Sent to Hackers’ Court.
Amidst Darkside’s recent monetary confiscation, many of the hacker’s affiliates are demanding compensation for their involvement in the cyber-attack and have taken Darkside to Hackers’ Court. What is Hacker’s Court? The hacker forum, XSS.is, serves as an escrow for the Russian ransomware group, and operates as the judicial platform for settlements between the organization’s leaders and their associates. The images below demonstrate how this “court” operates and the “organized” structure that it follows to grant eligibly for the Darkside settlement.
Let’s take a peek at how Hackers’ Court operates. These are all real images from the Dark Web.
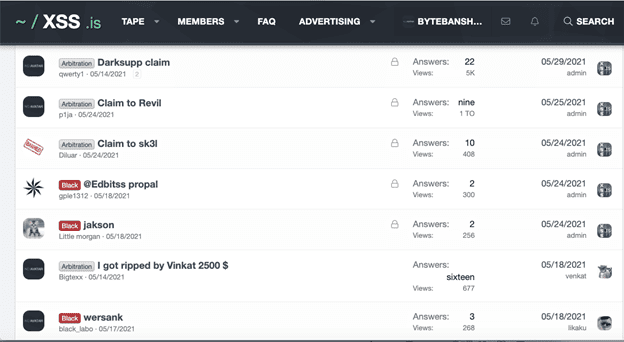
This first image shows that there are different disputes in Hackers’ Court involving a variety of ransomware groups (Darkside, REvil, and sk3l).
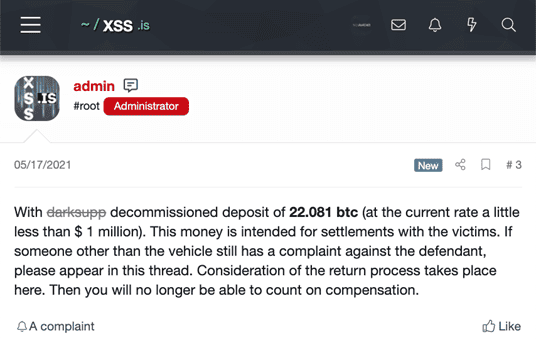
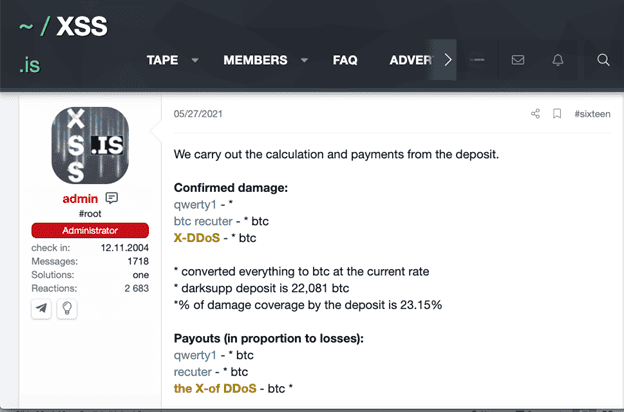
In the image below, the admin responsible for overseeing the cyber-court announces the amount (22.081 BTC) held in escrow for parties that are determined to be eligible for compensation for the “Darkside law suit.”
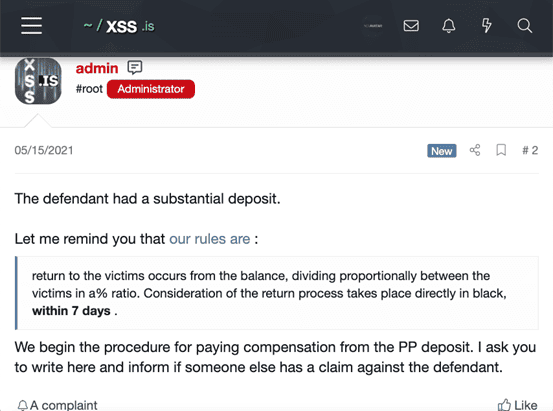
Then the admin “judge” establishes the rules that the plaintiffs must follow in order to be considered for a payout.
The “plaintiff” presents their case in the next image. They post a public summary, but send sensitive evidence directly to the Admin. The post below shows a claim made against Darkside by an affiliate who claims that they did not receive their share of the ransom amount paid by Colonial Pipeline.
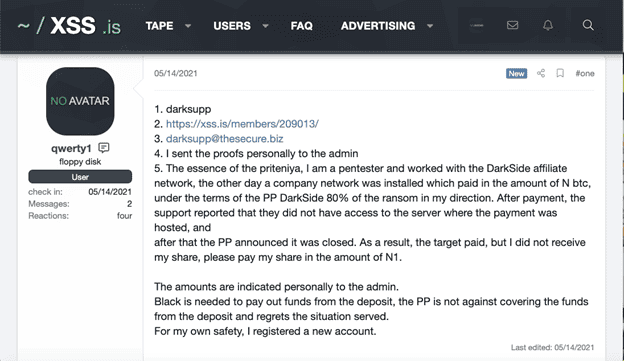
The next image shows another party that claims to have been a pentester for Darkside and assert that he/she did not receive proper compensation.
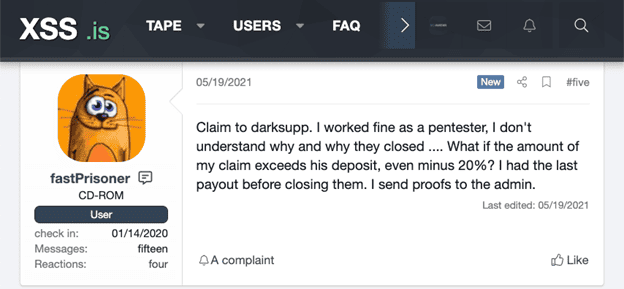
In sad news for this pentesting hacker, the Admin cannot consider the claim based on lack of evidence.
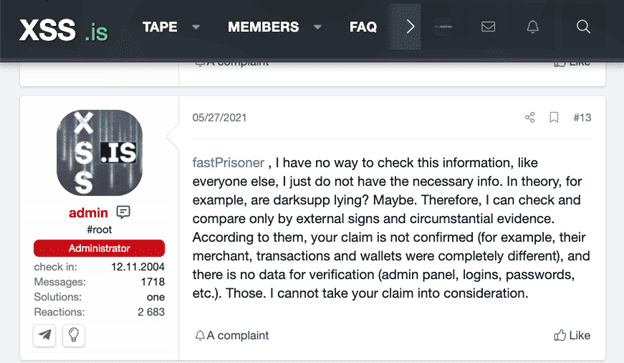
Ever efficient, the admin provides a status update for the previous plaintiffs’ claims in the image below.
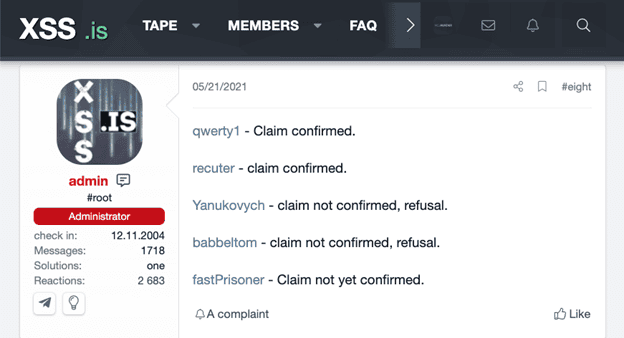
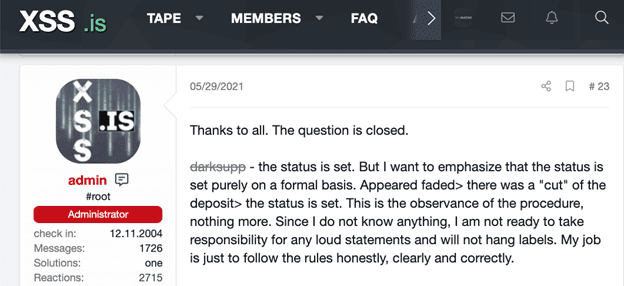
Finally, the Admin makes two finals posts that provide the verdicts, payouts for eligible parties, and a reminder that he is only the moderator and is adhering to the established rules.
The above images illustrate how Ransomware as a Service (RaaS) providers are under pressure from their hacker colleagues to follow through with their contractual obligations and promises. This reinforces the idea that these ransomware groups are becoming more aligned with a franchise-oriented model of doing business. A successful franchise model needs to maintain trust not just with “customers” but also their “affiliates”.
What Does this Ransom Payment Recovery Mean for Hackers?
Criminals rely on cryptocurrency to protect their identity while facilitating non-reversible payments. However, the recent bitcoin recovery tactic used against Darkside, draws attention to a particular flaw within cryptocurrency’s anonymity, specifically bitcoin transaction tracking.
The DOJ issued a statement on June 7th claiming that they were able to trace the Colonial Pipelines bitcoin transactions and seize the majority of the ransom. They also mention that the funds were recovered shortly after authorization of a seizure warrant and that they gained access to Darkside’s bitcoin wallet via private key. FBI Deputy Director Paul Abbate states that, “We will also continue developing advanced methods to improve our ability to track and recover digital ransom payments.”
Information on how authorities were able to gain access to the bitcoin wallet’s private key is still unknown; however, all bitcoin transactions are published publicly. This points out another possible weakness in Bitcoin, as anyone (who understands blockchain) could potentially trace a transaction back to a destination (wallet).
Crypto researcher JP Koning claims that, “Darkside accepts both Bitcoin and Monero, offering a 10% discount for the latter.” This is typically due to Monero being a more anonymous crypto method than Bitcoin. Monero has also gained popularity amongst other cybercriminals, such as markets on the Dark Web. The current largest darknet marketplace, White House Market, uses strictly Monero cryptocurrency for all purchases made on its onion site.
The Colonial Pipeline Ransomware Attack is Driving Regulatory Change
In the United States, legislation has been introduced to ban ransom payments; however, even if it goes through, the impact will be limited. The reason is that ransomware groups are purely financially motivated. Because of this, they will continue to adapt and use any resources they have in order to give their victims no other choice but to pay up.
Their latest tactic involves the traditional extortion method of shutting down networks and threatening to release company data; however, it adds a third element, the consumer. Therefore, Ransomware gangs are able to add further pressure to targets by threatening their business partners and customers data as well.
REvil has recently used this same approach with previous ransomware cases, including the recent ransom attack on the world’s largest meat supplier, JBS Foods. The organization announced on June 9th, that they had agreed to transfer $11 million in order to restore operations of their network and to protect their consumers. This movement of large-scale attacks on essential businesses is starting to become the norm in cybersecurity threats.
In the evolving war on cybercrime, some hackers seem undeterred by the threat of enhanced regulations. Threatpost.com recently released a telegram interview with the ransomware group REvil’s response to the recent US executive order. The group claims that they are not deterred by US legislation preventing companies from paying ransoms. They also claim, “that in light of U.S. actions and posturing to retaliate for the JBS Foods attack, the group will now lift the restriction on attacking U.S. targets.”.
We hope this information about the unique events surrounding the Colonial Pipeline ransomware attack has helped you gain a better understanding of the changing nature of ransomware. For more information on how to evaluate your ransomware risk, read our blog on ransomware risk factors & risk reduction strategies or contact us for a custom ransomware risk assessment and prevention report.

