Critical Incident Response Training: Your Top Questions Answered
 You’ve invested in firewalls, endpoint protection, and threat intel feeds—but what happens when your staff freezes under pressure? Cybersecurity isn’t just about tools—it’s about how your team responds when every second counts. In today’s threat landscape, critical incident response training isn’t optional—it’s essential.
You’ve invested in firewalls, endpoint protection, and threat intel feeds—but what happens when your staff freezes under pressure? Cybersecurity isn’t just about tools—it’s about how your team responds when every second counts. In today’s threat landscape, critical incident response training isn’t optional—it’s essential.
Imagine it’s 3 a.m. and your phone rings: ransomware has locked down your network, and your business is grinding to a halt. What happens next depends entirely on how well your team is prepared, and effective preparation can significantly reduce the damage and costs associated with an incident. According to IBM’s Cost of a Data Breach Report, organizations with a well-tested incident response (IR) plan saved an average of $1.5 million compared to those without one.
At LMG Security, we named incident response training one of our top cybersecurity controls (here’s why). In 2025, that priority hasn’t changed—if anything, it’s more critical than ever. Whether you’re building a new IR program or leveling up an existing one, this FAQ will guide you through what to look for in a critical incident response training program, what to expect, and how to make the most of your investment.
Critical Incident Response Training FAQs
1. What is Critical Incident Response Training?
Critical incident response training prepares your team to detect, respond to, and recover from high-impact cybersecurity incidents. These aren’t just phishing emails or minor malware infections—this is training for the big stuff: ransomware outbreaks, nation-state intrusions, or widespread disruption.
The goal? Minimize damage, reduce downtime, protect sensitive data, and improve coordinated decision-making under pressure. This kind of training ensures that when a real crisis occurs, your team reacts with precision, not panic.
2. Who Should Take This Kind of Training?
It depends on the type of training. A systemic misconception is that incident response training is only for the security team. Not true. For example, a tabletop training exercise should involve the whole team, including:
-
- Security analysts
- IT support and system administrators
- Legal, PR, and HR (for communication and compliance)
- Executive leadership
Think of it like a fire drill—everyone has a role, and if even one person is unsure of what to do, the entire response can fall apart. The same holds true during a real cyber incident. At LMG Security, we also recommend involving operational leadership and business continuity personnel, as they play a critical role in restoring services, maintaining communications, and managing the broader impact on the organization in a tabletop training exercise. Read our blogs on our favorite tabletop exercise scenarios of 2024 and our evergreen scenarios for detailed advice on running a tabletop exercise. Feel free to contact us to hear about our new 2025 AI/deepfake scenarios and other new options!
There are also specialized courses that have been developed for your IT or cybersecurity team first responders. For example, Cyber First Responder and Ransomware Response critical incident response training classes train professionals to quickly identify and respond to an incident, minimize the damage, and preserve evidence. This type of training can dramatically reduce the financial and reputation damage if you are breached.
3. What’s the Difference Between IR Training and a Tabletop Exercise?
Tabletop exercises are scenario-based discussions that walk teams through a hypothetical incident, focusing on roles, communication, and decisions, but without requiring hands-on technical work. They’re especially useful for engaging executives and non-technical staff. In contrast, specialized IR training includes technical simulations that allow security teams to gain hands-on training to practice containment and isolation procedures, investigation, auditing, and evidence collection, as well as recovery and restoration operations in a realistic environment.
4. How is Critical Incident Response Training Delivered?
Critical incident response training programs can include a mix of the following:
-
- Instructor-led training (virtual, on-demand, or in-person)
- Tabletop exercises with detailed scenarios
- Hands-on simulations or red/blue team engagements
- Post-incident reviews and improvement plans
Our team emphasizes realism. We recommend hands-on training that is grounded in real-world breaches and tailored to your organization’s risk profile. We include post-exercise debriefs to help teams review decisions and improve coordination.
5. What Should I Look For In a Strong Critical Incident Response Training Class?
A strong IR training class begins with instructors who bring real-world expertise to the table. They’ve led breach investigations, responded to ransomware attacks, or developed playbooks for high-risk industries. At LMG Security, our instructors bring this experience to life through a variety of classes delivered on-demand, live, and at major global conferences. Our training is shaped by real-world breach investigations, hands-on response efforts, and the development of IR strategies across diverse industries.
Strong IR training should also feature realistic, up-to-date scenarios—ransomware outbreaks, cloud breaches, supply chain compromises—and involve teams beyond just IT. Legal, HR, communications, and leadership should all play a role.
Ideally, IR training should align with your current incident response playbooks and IR escalation processes, and deliver practical takeaways that can be applied immediately. Customized training tailored to your environment and regulatory obligations is a significant plus if it fits into your budget. Ask if your provider can incorporate internal tools, escalation paths, and workflows to make the training as relevant and effective as possible.
6. How Often Should IR Training Happen?
At a minimum, once a year—and more frequently for critical infrastructure or high-risk sectors. Training should also be provided after any major incidents and should always be a part of onboarding new staff. Repeating exercises helps build muscle memory and team confidence. You can also alternate between tabletops, red teams, and various IT critical incident response training classes to build solid skills throughout your organization.
7. How Do I Know If My IR Team Is Improving?
Here’s how organizations typically mature from reactive to resilient IR:
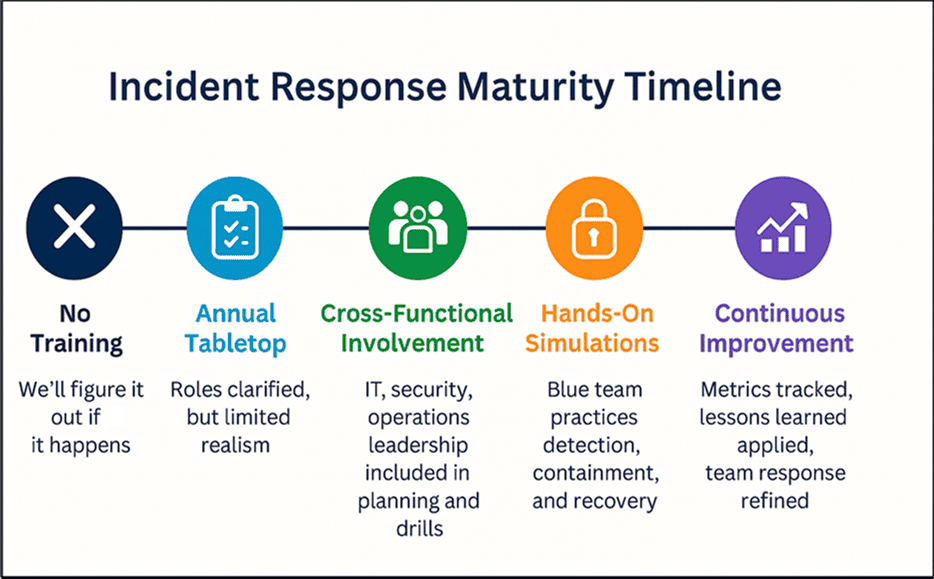
Figure 1: Visualizing the evolution from reactive response to full IR coordination.
Also, look for measurable outcomes over time:
-
- Faster Mean Time to Detect (MTTD) and Respond (MTTR)
- Fewer missteps or escalations
- Improved cross-functional communication
- More consistent documentation
- Greater situational awareness
Even well-trained professionals can struggle under pressure. Practice reinforces procedures and builds confidence. We recommend tracking performance across exercises. Some organizations even compare departments to spot coaching needs or identify best practices.
8. Does IR Training Help With Compliance?
Yes—and in many cases, it’s required. Frameworks and regulations that expect documented IR training include:
-
- HIPAA
- PCI-DSS
- CMMC
- NIST CSF
- ISO 27001
- State breach notification laws
In regulated industries, being able to demonstrate IR readiness can reduce audit risk and post-breach penalties.
9. How Does IR Training Support Business Continuity?
Critical IR training supports business continuity by ensuring:
-
- Teams know how to escalate and communicate
- Downtime is minimized since the team is trained in incident response
- Messaging is coordinated
- Customers and partners stay informed
A strong response preserves trust, protects reputation, and helps the business recover faster.
10. What’s the ROI of IR Training?
The real value of IR training is about keeping your business running when every second counts. IBM estimates the average savings at $1.5 million for organizations with a well-tested IR plan, driven by results like:
-
- Reduced downtime
- Lower penalties
- Faster recovery
- Stronger reputation
You can’t always prevent a breach, but you can minimize the damage.
Final Thoughts: Is Your Team Ready For the Real Thing?
Cyber incidents don’t follow your schedule. They can strike in the middle of the night—when your team is tired, the stakes are high, and there’s no time to think twice. They don’t wait until you’ve finished onboarding your new hire or wrapped up a quarterly project. When the worst happens, your preparation is all that stands between a quick recovery and lasting damage.
In this blog, we’ve covered how to identify strong training programs, who should be involved, how to measure success, and what red flags to avoid. The bottom line? Critical incident response training builds confidence, reduces costs, and helps your team stay calm and effective in a crisis.
Want to understand why we continue to prioritize IR training? Check out our blog from 2024 for more. Need help building or refreshing your incident response training? Please contact us for customized IR workshops, tabletop exercises, Cyber First Responder or Ransomware training classes, hands-on simulations, and more.

