By Sherri Davidoff / May 16th, 2018
Cyber Alert: New Ransomware Holds Individual File Shares Hostage
LMG’s Forensics Team has encountered a new type of ransomware infection (“Dharma .arrow”), in which criminals lock up individual file shares/devices with different keys. This means the criminals can charge you money to unlock each individual file share or storage device.
Want your Finance share back? That’ll be .5 BTC. Human Resources, too? Another .5 BTC.
After infecting the systems, the criminals send a link to a scanning utility. Victims must run the criminals’ scanning utility and send the report to the criminals, who evaluate the results and set a price based on the number of encrypted devices and shares. The decryption keys will only unlock shares and devices that were connected at the time that the system was scanned.
Here is a sample ransom note left by the new strain:
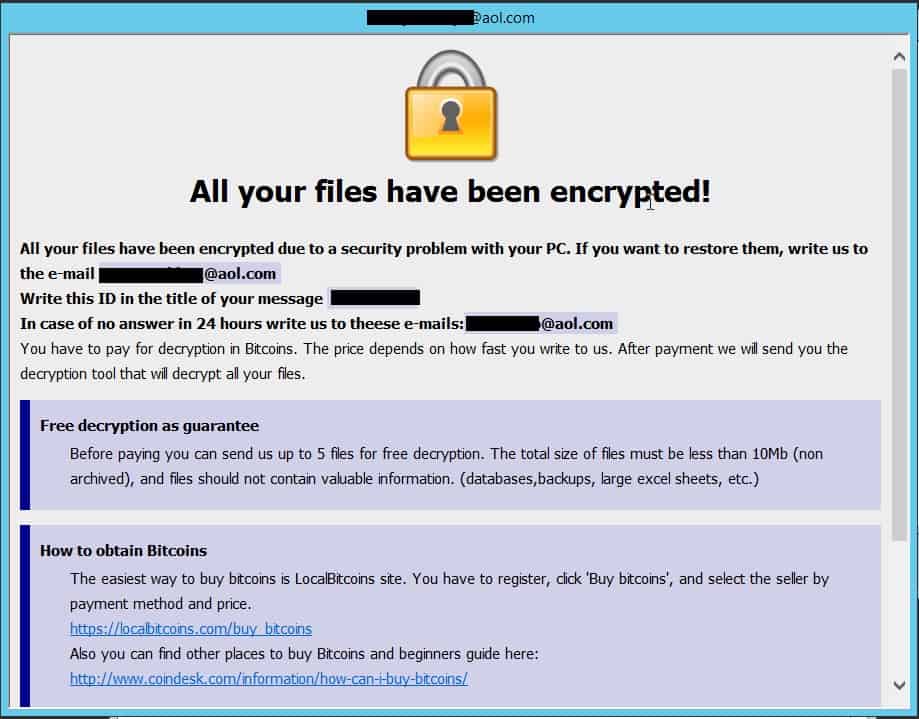
The Dharma .arrow strain was first spotted by Michael Gillespie’s ID Ransomware service in late April, and it seems to be gaining traction.
What You Need to Know:
- Strong encryption is used to take files hostage
- Each infected device/share has a unique decryption key, so the criminals can charge money for specific file shares.
- There still is no known method to decrypt files encrypted by the newer variants of Dharma ‘.arrow’ without paying the ransom and obtaining the private keys from the criminals.
Reduce your risk of ransomware infections by conducting:
-
- Regular vulnerability scans and penetration tests
- Training and awareness programs
- Backup checks
- Phishing tests
Contact LMG ([email protected]) for proactive ransomware defense, or for help responding to an attack.

