Exposing the Secret Office 365 Forensics Tool
 An ethical crisis in the digital forensics industry came to a head last week with the release of new details on Microsoft’s undocumented “Activities” API. A previously unknown trove of access and activity logs held by Microsoft allows investigators to track Office 365 mailbox activity in minute detail. Following a long period of mystery and rumors about the existence of such a tool, the details finally emerged, thanks to a video by Anonymous and follow-up research by CrowdStrike.
An ethical crisis in the digital forensics industry came to a head last week with the release of new details on Microsoft’s undocumented “Activities” API. A previously unknown trove of access and activity logs held by Microsoft allows investigators to track Office 365 mailbox activity in minute detail. Following a long period of mystery and rumors about the existence of such a tool, the details finally emerged, thanks to a video by Anonymous and follow-up research by CrowdStrike.
Now, investigators have access to a stockpile of granular activity data going back six months—even if audit logging was not enabled. For victims of Business Email Compromise (BEC), this is huge news, because investigators are now far more likely to be able to “rule out” unauthorized access to specific emails and attachments.
The secret tool provides evidence that could have saved hundreds—if not thousands—of companies from having to declare a data breach. It is very likely that small businesses were disproportionately affected, since they lack the budget to employ forensics firms and to utilize Office 365 subscriptions that support audit logging.
Until now, this level of granularity was thought not to exist. Turns out, however, that it did, and those who were in the know kept this knowledge a secret.
How did this happen, and is it right? Under what conditions may critical knowledge be withheld from the information security community and the clients we serve? The little-known existence of this Office 365 forensics capability raises important practical and ethical questions for the digital forensics industry, which will affect the community for years to come.
/* Check out LMG’s brand-new open-source “Magic Unicorn Tool,” which parses logs from the Office 365 Activities API (credit: Matt Durrin, LMG forensic analyst). */
The Epidemic – Business Email Compromise
 Around the world, hackers break into Office 365 email accounts. They search for wire transfer data and steal money. They download spreadsheets with Social Security Numbers, billing details, health information, and trade secrets. The problem has become so pervasive it is now an epidemic.
Around the world, hackers break into Office 365 email accounts. They search for wire transfer data and steal money. They download spreadsheets with Social Security Numbers, billing details, health information, and trade secrets. The problem has become so pervasive it is now an epidemic.
When the break-in is discovered, everyone wants to know: What did they see? What did they take? Was there a data breach?
All too often, mailbox audit logs don’t exist because Office 365 logging isn’t enabled by default. Absent evidence to prove otherwise, the organization is obligated to announce a data breach. The consequences can be enormous: huge bills for notification, regulatory fines, and reputational damage.
But what if the activity logs really did exist but were kept a secret? And what if a few digital forensics firms found out and figured out a way to access the data—but kept that information quiet, so they could secretly sell access at premium rates to private clients?
Shockingly, this is exactly what happened.
Rumors Surface
“Do you have the secret Office 365 forensics tool?” a breach response manager for a major company asked our team last year.
“What secret tool?” I replied. He explained that a few forensics firms they worked with possessed a secret tool that could pull extra activity details out of Office 365. These details were not accessible using the normal, published Office 365 query mechanisms. He said the tool was very secret and he wasn’t at liberty to share more.
We waved it off, figuring it was a marketing ploy. But over the next few months, rumors continued to circulate about a secret tool. A Microsoft programmer had left and joined a forensics firm, taking a secret internal Microsoft tool with him to his new employer, someone said. No one could confirm the rumors.
Our team couldn’t imagine that Microsoft would fail to disclose that such valuable data existed, especially when thousands of their customers were battling the specter of a breach. Given the potential for liability (not to mention the ethical considerations), that seemed unlikely. Forensics folklore, we concluded.
Forensics Firms Take a Hit
 Major insurers and law firms started to screen forensics firms based on whether or not they had “the secret tool.” Only a handful did — the rest were shut out. Over and over, forensics professionals started to hear, “Sorry, we can’t send you cases if you don’t have the secret tool.” And yet, there were no details, and no one with knowledge of the tool would even confirm its existence.
Major insurers and law firms started to screen forensics firms based on whether or not they had “the secret tool.” Only a handful did — the rest were shut out. Over and over, forensics professionals started to hear, “Sorry, we can’t send you cases if you don’t have the secret tool.” And yet, there were no details, and no one with knowledge of the tool would even confirm its existence.
What was this secret tool? Did it really exist? LMG’s team prides ourselves on doing excellent forensics work and providing the fullest information possible to our clients. If the tool existed, we had to get it.

Microsoft and The Magic Unicorn
As luck would have it, two of our colleagues were at Microsoft headquarters for a meeting with Microsoft’s security and IT team. While onsite,
they pulled Microsoft staff aside. An internal Microsoft security team member agreed to have an “off-the-record” conversation, in which he described the internal workings of Microsoft’s forensics data acquisition.
The secret tool could not possibly exist, the Microsoft team member insisted. In a separate conversation, a Microsoft Office 365 developer echoed the same thing. We had it straight from the horse’s mouth. The “Magic Unicorn Tool,” as we dubbed it, did not exist.
Emboldened, we called one of our attorney partners, who had been interested in using our forensics team on an Office 365 email compromise case. He flatly disagreed, stating that the tool existed. Then, he gave us a list of five major forensics firms that were (quietly) advertising that they possessed the secret tool.
The attorney sent his case over to one of the firms that had the tool. Whether or not it worked as advertised, the Magic Unicorn Tool was a clear competitive advantage.
A Call for Help
We needed help. I wrote a message to a forensics community mailing list: “Does this ‘secret tool’ actually exist? Any information would be greatly appreciated!” One person said they had heard it was an undocumented Microsoft API. A few people wrote privately to share vague rumors, but no one had specifics.
The next morning, a forensics community leader confirmed that the tool existed. “Its True. All of it. The Dark Side of o365. The Jedi who can perform this magic,” he wrote. “It DOES in fact exist.” But he said he himself could not share details.
We were stymied.
How could such a tool exist but remain secret? It was as if Alexander Fleming had discovered penicillin but kept the details hidden in order to make more money. It just seemed wrong.
We got to work, poring through dusty Reddit threads and analyzing ancient proof-of-concept code. Nothing worked. Maybe it wasn’t real.
“We’re going to run this to ground,” I announced confidently to our team — but inside, I had the feeling you get when you’re losing a hand of poker.
An Anonymous Gift
The tide turned on Friday, June 8. Out of the blue, an email popped onto the forensics community mailing list. It contained a single link, to an Anonymous video.
On the screen, a familiar white mask began to speak.
“Greetings,” it said. “We are Anonymous. Today we come bearing gifts… We are here to better humanity by uniting forensic examiners. For the good of citizens and public companies we demand there be no secrets.
“Stop this child’s play. Over the years we have seen companies delay artifact disclosure. This is dangerous like 0-day vulnerability disclosure… Some places view this as competitive intelligence. They reap the benefits, make lots of money and live like a Saudi prince… ultimately, this is usually at the mercy of some companies having to overreport, notify and pay lots of money.
“Forensic artifacts should be shared, scrutinized, vetted and improved — not hidden. Not thwarted… The gold mine of data that allows you to determine various actions despite audit logging not being turned on does exist. The API you seek is called Activities… There may be others but this is one of them. Now the community can do the rest and what is right.
“We are Anonymous. We do not forgive. We do not forget. Until next time.”
The mask stopped speaking. After a moment of silence, I dialed Karen Sprenger, LMG’s COO. “Anonymous gave us a present.” LMG’s team immediately began experimenting with the newly revealed API.
CrowdStrike’s Release
Ten days later, CrowdStrike released a beautiful blog post about the unmasked Activities API. “[W]e recently discovered a capability within Office 365 that allows for the retrieval of Outlook mailbox activity logs that far exceeds the granularity provided by existing, documented Office 365 log sources…” they wrote. “This capability represents access to an always-on, mailbox activity recording system that is active by default for all users.” Along with details of the new API, they released a Python module to automate retrieval.
As soon as CrowdStrike’s Python module was published, LMG’s team immediately downloaded it. Forensic analysts Ali Sawyer and Matt Durrin ran it against an Office 365 test instance set up in LMG’s research laboratory. It contained the granular details that we had only dreamed existed — and more.
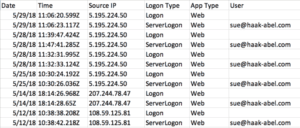
You can view the results below to see the tool’s capabilities, run against a test Office 365 account that was created for LMG’s upcoming Data Breaches course at Black Hat. The search activity report shows a threat actor searching for terms like “invoice” and “payment.”
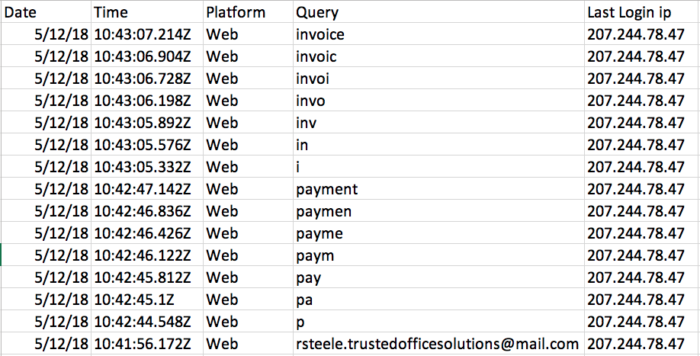
You can also see the threat actor viewing messages pertaining to an invoice and a W-9 form.
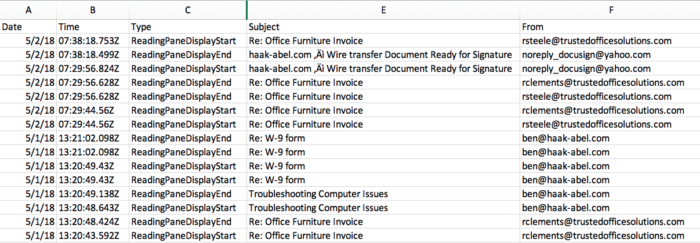
In the logon activity report, several different IP addresses are seen logging in to the account.
Ethics
The secret Office 365 forensics tool raises important ethical questions for forensic analysts and our broader ecosystem.
When one discovers critical new evidence that could make or break cases, it benefits society to share that information as quickly as possible. Yet in the case of the secret Office 365 tool, the very existence of this evidence was kept hidden by several respected forensics firms, as well as Microsoft itself, for well over a year by several accounts. Note that many individual Microsoft employees appear to have been genuinely unaware of this data’s existence.
– What standards should forensics professionals hold ourselves to for disclosure of “0-day forensic artifacts”?
At LMG, we feel strongly that forensic artifacts must be shared, not hidden, in order to serve our communities.
– What responsibility do attorneys, insurers and other trusted providers have for circulating and disseminating critical information?
We urge our colleagues throughout the industry to provide incentives for disclosure, not darkness.
– What is the responsibility of service providers, such as Microsoft, to support forensic investigations?
One could argue that preserving logs and forensic evidence is expensive — and yet, in the case of Office 365, highly granular log data was already being preserved, yet was simply inaccessible to all but a few.
Right now, companies have to pay more to enable account auditing in Office 365. By default, logging is not enabled for Office 365 customers, and is not included at all with the standard ProPlus and E1 plans. As a result, countless small businesses have been forced to report a data breach due to lack of logs. Budget-conscious organizations don’t have logs, and when they get hacked, they are more likely to have to notify. (As we now know, it turns out that certain critical logs actually do exist.)
– It’s time to establish standards for audit logging and preservation in the cloud.
Maintaining and providing access to audit logs is a cost for cloud providers. Similarly, fire suppression systems are a cost for building owners. In order to provide a reasonable level of safety and security for customers, we need to establish minimum standards. Otherwise, our society will continue to bear the burden of needless breach notifications.
Today, most cloud providers have no obligation to collect logs. Even if they do have granular logs, like Microsoft, they have no requirement to make these easily accessible to customers.
We call upon cloud providers to build transparency into their systems and provide customers and industry professionals with the tools they need to audit user activity by default.
New Release! The Magic Unicorn Tool
LMG forensic analysts have created a wrapper script, which leverages CrowdStrike’s Python module. The script, which we’ve called the Magic Unicorn Tool, is designed to parse the new data and produce human-readable reports that are useful for Business Email Compromises cases. Currently, the tool can parse and present:
– Mailbox searches, including the duration of message views and/or login sessions
– Logon events (both Logon and ServerLogon), recording date, time, IP address, and browser type
– All delivered and “Marked as Read” email activity
– Search events, logged by session ID with a reference to the most recent logon events
– Panel read events
– Attachment view events
Visit GitHub to get the Magic Unicorn Tool (credit: Matt Durrin, LMG forensic analyst).
The Future
What other tools exist that could help our clients? We as an information security community need to define, discuss, and then model ethical behavior for our industry.
As a first step, CrowdStrike released detailed information on the Activities API along with a Python script, and we at LMG Security have released a wrapper script called the Magic Unicorn Tool. We encourage other companies to do the same. Moving forward, we call for greater transparency among all digital forensics practitioners and cloud providers, for the benefit of all of our clients and community.
/* This article was authored by Sherri Davidoff, CEO, with contributions from LMG Security team members Karen Sprenger, Ali Sawyer, Matt Durrin, and Patrick Burns. Many thanks to the LMG Security team for all of their excellent work on this project. */

