How to Prevent Phishing Attacks Using Technological Defenses

Part Two of Our Three Part Blog Series on Phishing
When you consider how to prevent phishing attacks, the majority of tactics will be focused on employee behavior. Why? Let’s look at the data. The 2022 Verizon Data Breach Investigation Report found that 82% of breaches involved a human element – e.g. social engineering – and over 60% of those attacks were a result of phishing. At this point, most organizations realize phishing prevention has to be a priority.
In our previous phishing and spear phishing blog post we discussed the prevalence of these attacks, as well as some common tactics. While user training is the biggest way to prevent successful phishing attacks (and we will devote an entire blog to this in the third blog of this series), there are also several technology defenses you can employ. Technology defenses are frequently overlooked in most phishing blogs, so let’s dive in so you can ensure you’re covering all your bases.
How to Avoid Phishing Emails
There are many things a systems administrator can do to help prevent phishing emails from even getting to users in the first place and to help limit the severity of attacks if the emails do end up getting through. The first and most important aspect is email and spam filtering. Most systems administrators understand this, but it is important to have spam filtering enabled for emails to keep generic phishing attempts and other spam from landing in your inbox. Highly targeted attacks are more difficult to prevent as spam filters may not know if an email is coming from a malicious domain or a doppelgänger domain, for example. This is where tools like DNSTwist can come in handy. Once a domain is entered by a systems administrator, DNSTwist will generate hundreds of doppelgänger domains that attackers could use for phishing attacks. These domains can then be added to the blocklist of the spam filter in order to prevent these doppelgänger domains from ever being delivered. Some organizations also decide to purchase some of these doppelgänger domains to prevent an attacker from using these domains for phishing attacks.
Here is an example of DNSTwist in action for lmgsecurity.com:
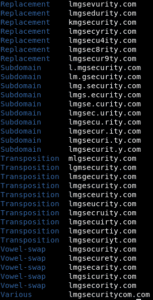
Setting up Technical Barriers to Reduce Phishing Attempts
Let’s take a deeper technical look at this process. In addition to filtering doppelgänger domains, organizations should also:
- Enable and require all three of the following protocols by all mail servers in an organization:
- Configure mail servers with Sender Policy Framework (SPF). This prevents forged emails from ever being accepted. It is done by verifying DNS entries on the mail servers and checking incoming emails with a list of verified sending DNS entries and IP addresses.
- Domain Keys Identified Mail (DKIM) should be set up as well and required for all mail servers. Both SPF and DKIM verify the legitimacy of emails, but SPF is the defined list of servers that are allowed to send email on behalf of your domain. This list of authorized servers is published via DNS and verified by the recipient’s email server when received. This is a different from DKIM, which allows the recipient to verify the message was not altered after it was sent from the approved email server. DKIM is a way for emails to be signed and verified as a genuine sender using cryptographic keys. Each approved server generates a public and private keypair; the public keys are published via DNS. Once an email is sent, the server signs the email with the private DKIM key and the recipient verifies the digital signature against the public DKIM key published in DNS to ensure the email is actually valid.
- Domain Message Authentication Reporting & Conformance (DMARC) should also be set up on all mail servers in an organization. DMARC is an extension of the previous protocols. It allows a systems administrator to set up instructions. Once DMARC instructions are published, a DNS record is made that tells receiving servers what to do with messages from your domain that don’t pass SPF or DKIM.
- Implement a secondary form of email verification. For added security, an organization can implement an extra form of email verification where emails are verified client-side on each user’s computer. This can be accomplished by implementing a service such as PGP, GPG, SMIME, etc. which uses public and private keys (Public Key Infrastructure, PKI) for each sender to cryptographically sign emails. The recipient can then verify the authenticity of the emails. These digital signatures are like DKIM but are applied by the user, whereas DKIM signatures are applied by the mail server.
- Maintain up-to-date patches. Ensuring that patches are current for systems and antivirus software is important since attackers may attempt to exploit systems through browser exploits or file attachments. This can lead to malware being installed on a host or spreading throughout the network. In addition to maintaining up-to-date systems and software, the configuration of proper egress filtering is important as attackers can use a hidden Server Message Block (SMB) resource link which may allow an attacker to capture a user’s NetNTLM password hash. Prohibiting TCP and UDP ports 445 and 135-139 from sending data outside of the network would prevent this attack.
- Network segmentation. Divide your network into different segments (or zones) to limit the flow of traffic to each zone, and ensure that each employee only has the access they need to do their job. This will enable you to reduce the number of users with access to sensitive information or systems and decrease your risk of sensitive data being exfiltrated. Check out our blog, 7 Network Segmentation Best Practices That Stop Malware’s Lateral Spread, for more tips and information.
Services such as Microsoft ATP, Mimecast, Proofpoint, Barracuda, and others can help prevent many phishing attacks by scanning emails and URLs for malicious content. URL inspection and rewriting services help protect users from harmful emails or links by following the targets of these links, scanning for malicious content, or even going as far as executing the link’s contents in a sandbox environment. Services like these can add an extra layer of defense towards preventing malicious emails and attacks on an organization. However, this needs to be done in parallel with user training or your users may be confused and concerned when they see the URL change.
How to Avoid Phishing Attempts from Within the Domain
The methods described in this post can help prevent many external phishing attacks, but as we discussed previously, you can also face attackers using valid accounts to conduct phishing attempts from within a domain. In this case, it becomes more difficult to determine if emails are spam since they are originating from valid internal accounts. The easiest and most secure ways to prevent internal spam is to prevent attackers from gaining access to mail accounts in the first place. Enforcing multifactor authentication (MFA) and strong account credentials go a long way in preventing unauthorized access to accounts. Even if an attacker has valid credentials for a user, the use of MFA would prevent the attacker from logging into the account. If you register for our free MFA workshops on 6/7/22 (or catch it on demand afterwards if you miss it) we’ll provide step-by-step instructions on how to set up MFA for G-Suite, Microsoft 365, and Duo.
In addition to MFA, logging and notifications should be configured to monitor for suspicious logins (watch our video for more on logging and monitoring). This is commonly based off GeoIP data—if an account attempts to login from a country or area where a user should not be logging in, a temporary block should be put on that account, and IT should be notified for further investigation. Furthermore, your mail server or service should be configured so that when a user sets up any forwarding or mail rules, IT should be notified of these changes to investigate and validate their purpose. Many attackers exploit the use of mail rules to hide their presence on a user’s account.
In addition to our previous recommendations, there are additional areas that system administrators can enhance security and limit an organization’s attack surface. Unless there is a business need for them, the POP and IMAP protocols should be disabled. If an attacker authenticates using POP/IMAP, the entire contents of a user’s mailbox are downloaded to the attacker’s system. This creates additional issues after the fact when trying to determine what sensitive mailbox contents an attacker accessed as there are no data access logs available after the mailbox contents are downloaded. Network monitoring and alerting should be implemented on the organization’s internal network. This can be useful in many cases, but for phishing attacks, the ability to see odd traffic on the network can help notify IT of a potential phishing attempt and stop it before an attacker is able to gain a foothold or compromise an account. In addition, the ability to block access to a phishing page could limit the number of affected users. Finally, prohibiting mail relaying and anonymous mail submission on mail servers can help prevent unauthorized relaying or forging attacks.
Although many steps can be taken to limit the ability to send phishing emails to an organization, some phishing emails may still bypass technical controls and get into users’ inboxes. Training users to identify suspicious emails and take appropriate actions is vitally important and will be covered in the next post in this series. Stay tuned for our third and final installment on how to prevent phishing attacks.
Phishing Series links:
Part 1: Understanding Phishing Attacks & Spear Phishing
Part 2: How to Prevent Phishing Attacks: Technological Defenses
Part 3: User Training: The Best Defense Against Phishing Attempts
