It’s Time to Update Your Incident Response Playbook
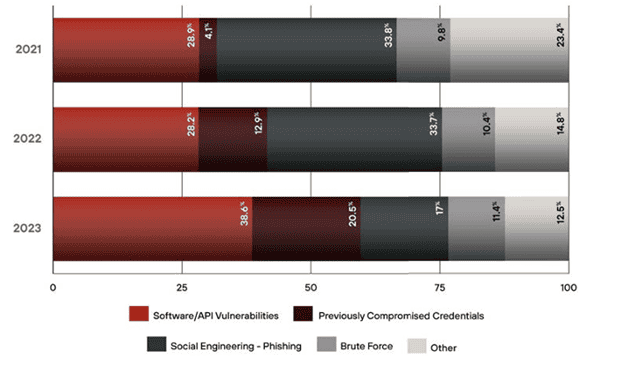
Source: APT42 chart on initial data breach attack vectors in 2023.
In 2023, almost 40% of attacks came from software/API vulnerabilities. In addition, this same report from Palo Alto also found that in close to half of the cases, hackers exfiltrated the data in less than 24 hours. These fast attacks that leverage zero-day and slowly patched known vulnerabilities are popular attack trends and preventing them is challenging. The shift to the cloud has also changed incident response, and many teams are unprepared for curveballs when working with cloud providers. What’s your best bet? Assume you will have an incident and make sure your incident response playbook addresses today’s latest threats.
IBM found that having an updated incident response plan and a properly trained IR team can save your organization $2.6 million in data breach costs. Whether you are looking to create an incident response playbook for the first time or update your existing plan, let’s dive into key elements to include, timely updates such as zero-day vulnerabilities and cloud incident response, as well as what’s in our LMG Security IR “go bag!”
What is the Difference Between an Incident Response Plan and an Incident Response Playbook?
These days, many organizations use the term interchangeably. But often an IR plan is a strategic document that outlines your goals and major activities in the event of a breach, while an incident response playbook is a detailed plan and guide with specific steps, contact information, and more. Playbooks range from short guidance documents to incredibly detailed step-by-step directions. Some organizations also have incident response playbooks that specify unique actions depending on the type of breach (i.e. zero-day breach versus ransomware). You should decide what level of guidance your organization needs and whether to invest internal resources or outsource the development of your organization’s IR plan or playbook.
Three Crucial Controls to Support Your Incident Response
There are three crucial controls that you should have in place as the minimum baseline for proactive incident response preparation.
- Monitoring and Detection tools: Implement continuous monitoring and detection systems (a SIEM, IDS/IPS) to identify potential security incidents.
- Threat Intelligence: Utilize threat intelligence feeds and platforms to stay informed about emerging threats and vulnerabilities.
- Incident classification criteria: Establish criteria for classifying incidents based on their severity and potential impact so you know when to activate your incident response plan.
Now that we’ve covered the topics and minimum tools you will need in your plan, let’s jump into a step-by-step guide on what to include in your incident response playbook.
Cloud Incident Response Challenges
One of the biggest changes in incident response has been the shift to the cloud. For example, if you are dealing with a cloud breach you may encounter unique challenges, including data preservation and limited vulnerability management options in your specific cloud service (which means logs may not exist, there may be limited data inventories, etc.). Even worse, our team finds that the cloud providers’ tools can’t always be trusted. Some can:
- Produce inconsistent results for similar queries.
- Have issues downloading large log sets as many limit the downloads to around 5,000 lines.
- Display limited information for each result.
- Have limited or no ability to filter information effectively.
So, what does this mean? Our team recommends ensuring that your incident response playbook is updated to address cloud-based response issues, and then PRACTICE your response. Seriously, practicing makes all the difference. Not practicing your response is the equivalent of a sports team just playing in games without having practices. The best way to practice your response is with a tabletop exercise. Read our blogs on how to conduct tabletop exercises and our favorite scenarios: best tabletop scenarios for 2024 and evergreen tabletop exercise topics for more details. Keep in mind that for your plan or playbook to be effective, your IT team also needs to be trained on how to quickly spot an incident as this is crucial to activating your plan and reducing damage.
Zero-Day Vulnerability Response
Until now, few organizations considered zero-day vulnerability response when designing their incident response playbooks. Today, it’s a crucial component given the speed of exploitation. Fortunately, CISA has provided an example of how to integrate vulnerability response into your incident response playbook. In the image below, you can see a simple incident response process graphic from the CISA Incident and Vulnerability Response Playbook that can be included in your incident response playbook and guide your team on what to do in the case of an incident. This chart provides your incident response team with a clear process to determine whether a newly identified vulnerability may have led to an actual intrusion, and steps to quickly reduce risk.
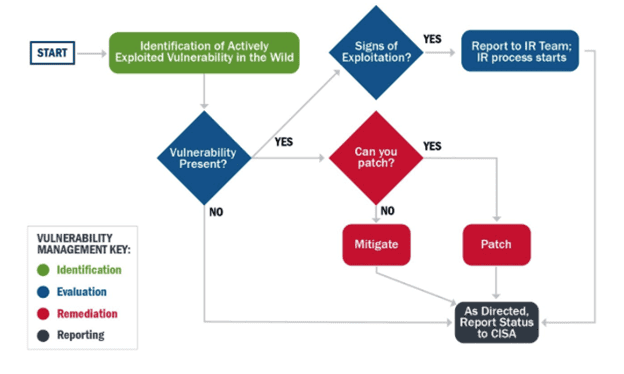
Source: CISA Incident and Vulnerability Response Playbook, page 22
4 Strategic Incident Response Initiatives
While there are many tactical steps you can take to reduce your risk, you should start with these four key strategic initiatives to proactively prepare for an incident.
- Policy development: Establish clear cybersecurity and incident response policies and procedures. Ensure your policies align with your cyber insurance policy requirements. If you need help, contact our advisory team for guidance.
- Incident response playbooks: Incidents happen so quickly today that CISA recommends everyone have an incident response plan or playbook. Develop and regularly update an incident response playbook that outlines roles, responsibilities, procedures, and communications.
- Training and awareness: Conduct regular training sessions and simulations to ensure all team members are familiar with the incident response plan and can respond effectively. Ensure that at least several of your technical team members are specifically trained to respond to cyberattacks.
- Tools and resources: Ensure the availability of necessary tools, technologies, and resources to support incident response activities. See our sidebar for a list of the items in our LMG IR Go Bag!
Your team should define what you can realistically do in all four of these areas right now, and you should create a plan to phase in any missing initiatives as soon as your organization’s budget and resources allow.
We hope you found this information helpful. If your team is stretched thin or you want experts to support your policy development, contact the LMG Security team and we can lighten your workload and ensure you’re aligned with today’s best practices!
