New 2020 Twitter Attack & How to Keep Your Social Media Accounts Safe

Twitter Attack Hits High-Profile Accounts
This compromise – called a ‘coordinated’ attack by Twitter – hit multiple high-profile accounts nearly simultaneously and appeared to bypass security controls like multi-factor authentication (which makes it even harder to devise solid strategies for how to keep your social media accounts safe). A partial list of the accounts compromised include: Bill Gates, Elon Musk, Joe Biden, Barack Obama, Jeff Bezos, Kanye West, Warren Buffett, Wendy’s, Uber, and Apple, and included many cryptocurrency accounts as well, like Coinbase, CoinDesk, Bitcoin, and Ripple. (Many of the accounts were reportedly using multi-factor authentication.) All of the accounts posted a similar message around the same time:
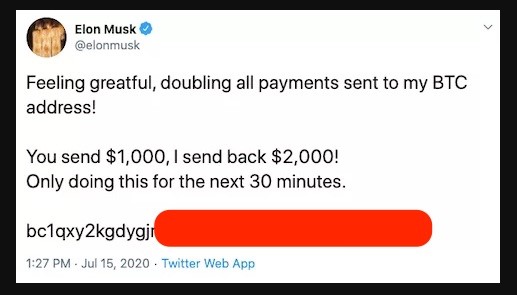
Reportedly the wallet received over $121,000 in the first 30 minutes of the attack. Prompting many prominent figures to ponder how to keep your social media accounts safe from these types of attacks.
How Did the Hackers Gain Access?
While the investigation is on-going, Twitter Support announced, that at this time, they believe that access was gained to their internal systems and tools, via a ‘coordinated social engineering attack’, although we have no details on what attack vector was used. This makes it even harder to figure out how to keep your social media accounts safe from this type of attack. However, multiple users posted what is alleged to be screenshots of Twitter’s internal dashboard:
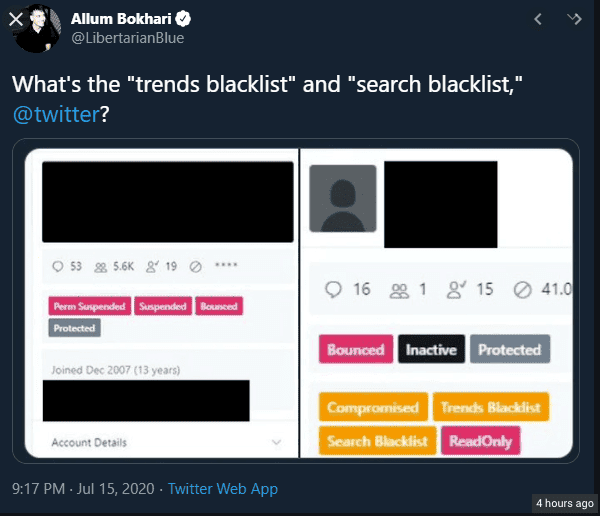
As of late Wednesday night, Twitter was actively removing tweets that included the screenshot.
Twitter’s Response
During the early stages of their incident response, Twitter locked the compromised accounts, removed scam related tweets, and internally restricted access to their systems. They also restricted any verified users (accounts with a blue check mark), and removed their ability to post, leading to many humorous posts by non-verified accounts. Restricted accounts were allowed to retweet, causing many non-verified users to offer to post the “blue-checks’” thoughts for them to retweet, or in some cases, posting the alphabet one letter at a time, to allow those restricted to try to piece a message together through retweets.
Unfortunately, this restriction had a more serious effect. While many of us think of social media as entertainment, the inability of verified accounts to tweet is a stark reminder that it is also an indispensable tool for quickly disseminating information. For example, due to the restriction placed on the verified accounts, the National Weather Service was unable to post severe weather warnings, at a time when they were tracking a large tornado in central Illinois.
How to Keep Your Social Media Accounts Safe
From all appearances, the users affected by this compromise took appropriate steps to secure their accounts and followed prevailing guidance on how to keep your social media accounts safe. They used strong passwords; they used multi-factor authentication, and I strongly encourage all of you to do the same. Unfortunately, those safeguards didn’t work in this case. This particular attack was on Twitter itself. In that situation, you are reliant on the social media platform itself to protect you.
So here are some general guidelines for social media use, as well as tips for how to keep your social media accounts safe:
- Use strong passwords and multi-factor authentication
- Consider Taking Your Account Private. If you use your account for fun, and don’t need or want your content visible to everyone, make your account private. With a private account, only your followers can see your posts, and new followers must request access and be approved by you.
- Use Your Account Wisely. Think about what you post to your account. Is it something that needs to be said? Will it come back to haunt you? Does your audience have trouble differentiating between your humorous and serious posts?
- Have a Back Up Plan. If you are a business or organization that needs to use your account to share important information, ask yourself what you would do if that service weren’t available and create a Plan B. During this Twitter outage we learned that many of our favorite verified accounts have non-verified, less publicized accounts (or in some cases accounts for their pets) that they switched to and used for tweeting. While the accounts didn’t have the same reach, they could then retweet from their verified account. If social media communication is vital to your organization, your strategy needs to be more concrete – phone lists, email notifications, texts. Create a plan for the best way(s) to get your message out if it’s urgent and you don’t have access to social media platforms.
- Educate Yourself and Your Staff to Resist Social Engineering. If the investigation bears out as it has so far, this was not a failure of systems or technology. It was human error. Humans make mistakes and will continue to do so. Organizations should implement technical defenses to reduce phishing, but also make sure that you, and everyone you work with understands phishing and social engineering. Don’t click on links, don’t provide information to unsolicited callers over the phone, don’t ever give out your username and password. Above all, if you make a mistake and click the link, report it to someone. The quicker that action can be taken, the quicker any damage can be contained.
What’s Next?
While I’m sure it does not seem like it to the security staff at Twitter, they got lucky. Overall, this is what cybersecurity experts would call an unsophisticated attack. The attackers had brief, unfettered access to the most powerful accounts on the platform and used it to try to scam followers for bitcoin. Given all of the challenges currently facing our country and the world (including the upcoming US election) an attacker with the level of access gained here, could have used that access to far worse purposes. By tipping their hand now, the attackers gave Twitter, and all platforms, a wakeup call – and time to put new security measures in place to protect against future attacks. Tighten your seatbelts; 2020 isn’t over yet.
Contact us if you need help with social engineering, penetration tests or advice on cybersecurity policy development. Our expert team can help.

