Understanding Phishing Attacks & Spear Phishing
 Phishing attacks and their more targeted cousin–spear phishing attacks–continue to be one of the top causes of a data breach. In fact, a recent survey found that 83% of respondents experienced a successful email-based phishing attack in 2021. Unfortunately, phishing and spear phishing will continue to be one of the top cybersecurity threats for 2022, so it’s important to have a phishing prevention plan in place.
Phishing attacks and their more targeted cousin–spear phishing attacks–continue to be one of the top causes of a data breach. In fact, a recent survey found that 83% of respondents experienced a successful email-based phishing attack in 2021. Unfortunately, phishing and spear phishing will continue to be one of the top cybersecurity threats for 2022, so it’s important to have a phishing prevention plan in place.
Why are Phishing Attacks One of the Top Cybersecurity Crimes?
- These attacks have solid success rates in the cybercrime industry
- They can be performed with minimal hardware or technological knowledge – criminals can even buy affordable phishing-as-a-service kits that bypass MFA
- They are very low cost and provide an easy return on investment (ROI)
This blog is the first in a three-part series about phishing attacks. It provides an overview on phishing, while parts two and three will provide more technical details on phishing prevention. Before getting into the nitty-gritty of phishing attacks and phishing prevention, let’s take a step back and look at just what phishing is.
One Phish, Two Phish – The Types of Phishing Attacks
Phishing is a type of social engineering attack and can be split into three different main categories: email phishing, voice/phone phishing (also known as “vishing”) and smishing / text phishing.
- Vishing or voice phishing is an older, but still quite popular, form of phishing using phone calls. Scammers may pretend to be a utility company and threaten to shut off service without an immediate payment over the phone, or claim to be a family member that needs bail money. There are myriad variations for vishing scams that seek to steal your information and money.
- Smishing, aka SMS phishing or text phishing, is done via a fraudulent text message. These are frequently short messages that ask you to use the included link to confirm your credit card account information, or claim to be FedEx and suggest that you click a link to check for an update on your delivery, etc. Sadly, most smishing links download malware onto your phone when you click, and then the attacker can steal your data.
- Phishing is when a malicious actor sends a fraudulent email in an attempt to entice a user to perform some behavior. One popular email phishing attack is where criminals attempt to steal a user’s credentials by setting up a fraudulent credit card or bank site and ask recipients to check their account and log in using the provided link. The site then has a script running to capture those credentials. A malicious actor can then use a user’s credentials to further attack an organization, such as deploying ransomware. Email phishing attacks could also be used to facilitate other attacks, or to spread malware via malicious file attachments.
In this article, we will focus on email phishing, but read this blog for more on vishing.
Criminals Go Big With Spear Phishing & Whaling
In an email phishing campaign, malicious actors have multiple options as to who they can target. The choice of targets can be split up into three main types of phishing attacks:
- Generic Phishing – This is when a malicious actor throws a wide net to try and target as many users as they can with a generic message (hoping a few fall for the scam). A single victim could be enough to consider a phishing campaign a success. With that in mind, generic phishing campaigns are almost always successful. But even though an attack may be successful, it may not lead to the privileges or access that a malicious actor wants (most users should have limited access). Some criminals want to think bigger.
- Spear Phishing – These attacks are characterized by malicious actors targeting an individual or subgroup of users in an organization – frequently users with access to sensitive information (IT administrators or accounting management). The scammer conducts research on the target, and one common tactic is to pretend to be a trusted peer or manager to get the target to provide information or money. This tactic is known as pretexting. For example, the attacker may pose as the CEO and ask for a list of aging accounts with payments due and contact information. Spear phishing attackers frequently research the target on social media or using Google and target attacks towards their interests, whether that is sending an email that appears to be from their favorite charity, store or gym.
- Whaling – This is when a malicious actor targets one specific, high-ranking executive in an organization (usually a target who is suspected to have increased privileges or access to sensitive data like the CFO, CEO, CISO, etc.) and tries to tailor their attack to that one target. It’s spear phishing that targets C-suite. This form of phishing generally has a lower success rate, as it is much more limited than a generic phishing attack, but could lead to the compromise of a high-level user if successful.
Why Are Phishing Attacks So Successful?
Phishing attacks and spear phishing attacks continue to be successful because they exploit the way users are trained to trust emails, especially when they appear to be coming from inside the organization. This, coupled with the fact that people (in general) are predisposed to being helpful and responsive through email, makes phishing a highly popular attack vector. Phishers use many techniques to exploit this trust even further. One very common technique is the use of doppelgänger domains (website names), which look almost identical to the domains that targets are used to seeing. Unless users are critically analyzing the domain names on emails they receive, they are unlikely to catch the subtle differences in domain names. In addition, malicious actors frequently make use of hyphenated domains and subdomains, such as outlook.lmg-security.com, in an effort to hide and legitimize their doppelgänger domain.
Trust can also be impacted by the way emails are displayed to users. Malicious actors can set whatever display name they want as the sender, which can aid in adding authenticity to phishing attack emails. Many mail applications, such as Outlook, can include an employee’s picture when emails are received from a known sender’s address. As sender addresses can be forged, this can be exploited to lend credibility to the phishing email.
Forged emails and websites are extremely easy to clone and make indistinguishable from their legitimate counterparts. For example, a malicious actor could clone a legitimate password reset email that a user has been conditioned to believe is real. A link in this email could actually lead to a malicious clone of the legitimate login page used for password resets. Familiarity can create trust, which allows malicious actors to instill more legitimacy in their attacks.
Users are trained to trust sites that have a valid SSL certificate (as demonstrated by https:// in the URL or a green lock icon) associated with them. Malicious actors can generate valid (and free) SSL certificates for their phishing sites, which immediately creates legitimacy. One survey found that 72% of phishing sites were using digital certificates and TLS encryption – just seeing HTTPS is no longer a guarantee of safety.
In addition, with spear phishing or whaling, malicious actors have the luxury of being able to perform copious amounts of research (reconnaissance) on their targets before launching an attack. This reconnaissance can be leveraged to add legitimacy and is often paired with other factors, such as dates, locations, known services, etc. For example, if it is tax season, a malicious actor could create a campaign related to an employee’s W-2 form. If an organization is known to use a certain service, like Slack for internal communication, a malicious actor could craft a phishing campaign that impersonates or references that service.
The Anatomy of a Successful Attack
Here at LMG, we have also seen an uptick in organizations being compromised by phishing attack campaigns originating from legitimate email accounts within the organization. If a user’s account is compromised (through whatever means) a malicious actor may be able to start sending phishing emails posing as the compromised user, which is very difficult to distinguish as a phishing email since they are originating from a legitimate internal account.
Here is an example of a phishing email and a web page that shows some of the techniques mentioned in this blog:
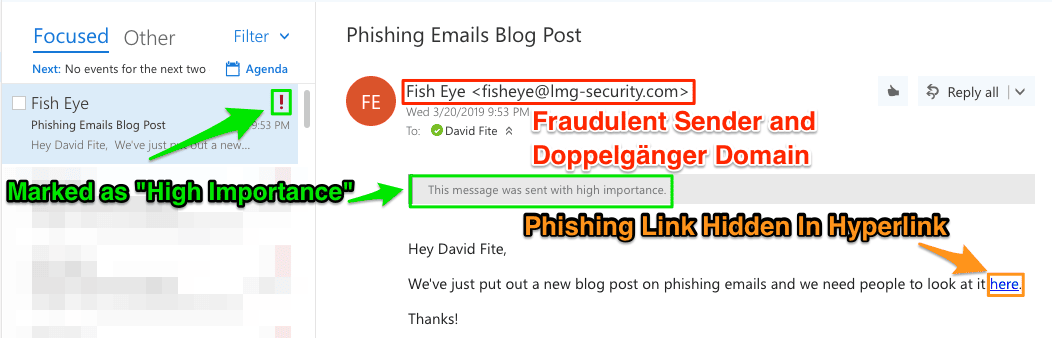
This email has a doppelgänger domain of lmg-security.com, but lmgsecurity.com is our real domain. It has the sender address that looks like it came from a user within LMG Security named “Fish Eye”. It’s marked as high importance, which is stated in the email and has the “High Importance” exclamation point before opening the email. The phishing URL is also hidden within a hyperlink on the word “here”.
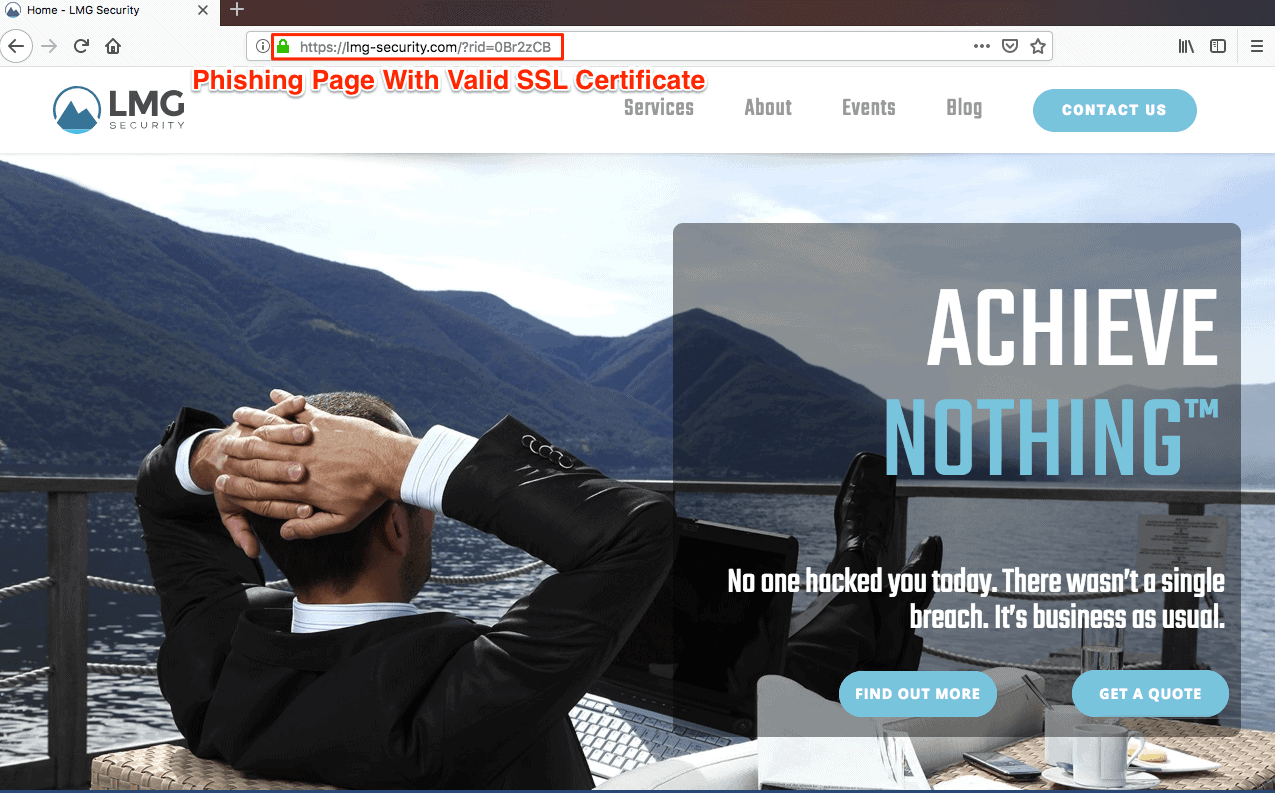
After clicking on the phishing link, the user is brought to a page that looks exactly like LMG’s legitimate homepage. As shown in the URL, the site is using the same doppelgänger domain as the phishing email. The site is also using a valid SSL certificate demonstrated by the use of the green lock icon.
As you can imagine, a sophisticated malicious actor can use variations of these techniques to exploit the permissive nature and trust of email, which could result in the compromise of credentials, or to spread malware, such as ransomware. Be sure to read our tip sheet for more information on how to spot a phishing email.
Thank you for reading part one of our three-part series on phishing. In subsequent blog posts we will explore how to best protect against phishing attacks through both technical controls and one of the most important factors, general cybersecurity awareness training for your entire team.
Phishing Series links:
Part 2: How to Prevent Phishing Attacks: Technological Defenses
Part 3: User Training: The Best Defense Against Phishing Attempts
