Ransomware Decryption is Like a Box of Chocolates...
You never know what you’re going to get when a criminal sends you a tool and tells you to run it. More and more often, victims of ransomware pay to receive a ransomware decryption tool— only to find that it installs even more malware.

The (infected) decryptor tool.
In one recent case, LMG’s team was called to help a healthcare organization that was hit with ransomware. The attackers locked up all of the company’s critical files, including medical records, billing information, financial data— even the backups.
The ransom negotiation was quick and professional. The criminals demanded .8 Bitcoin (about $3,700 at the time). As soon as the criminals received their money, they immediately sent a link to their ransomware decryption tool, saying, “let us know how it went.”
As a safety precaution, LMG’s team didn’t run the decryption tool on our client’s data right away. Instead, we installed it in our malware laboratory, to see if the criminals had included any hidden “extra” malware in it.
Turned out the decryption tool itself contained a nasty Trojan– the IcePoint RAT, a backdoor that would have enabled the criminals to gain full remote access. Our client would have recovered their files, but then whoever controlled the new malware could have come right back in, stolen data or held them for ransom all over again.
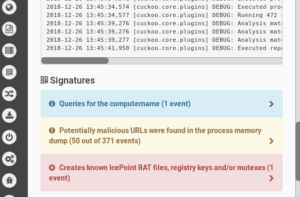
Malware lab – LMG’s team finds the IcePoint RAT hidden in the ransomware decryptor
Why would the criminals want to re-infect their victims? In all likelihood, they didn’t. The ransomware used in this case is widely available on the dark web, so it was purchased from malware developers. The developers, we figured, added the Trojan, so that they could piggyback off their customers’ hacking. Once their customers were done holding the victim for ransom, the developers would then have control of the victim’s systems and could resell access.
Happily, we were able to decompile the ransomware decryption tool, remove the malicious lines, and recover the client’s data safely. However, this case illustrates why ransomware decryption can be so tricky and time consuming. As our forensic analyst Matt Durrin said, “Ransomware decryption is like a box of chocolates. You never know what you’re going to get.” (He made that up.) Even after you’ve received the ransomware decryption tool, there’s still a lot of work left to be done!
Takeaways for defenders:
- Don’t trust tools given to you by criminals! (This may seem obvious, but when you’re being held for ransom, it’s tempting to quickly run whatever tools they send you. Don’t.)
- Always run ransomware decryption tools in a malware laboratory first, to check for malicious behavior.
- Decrypt your files in a non-networked environment whenever possible.
- Scan any files you recover using multiple antivirus vendors before putting them back into production. Criminals can leave additional malware behind for you to discover later.
- After you’ve recovered, monitor your network carefully for any signs of lingering compromise.
If you have questions about ransomware or need help recovering, contact us!

