Get Our Full Ransomware Guide
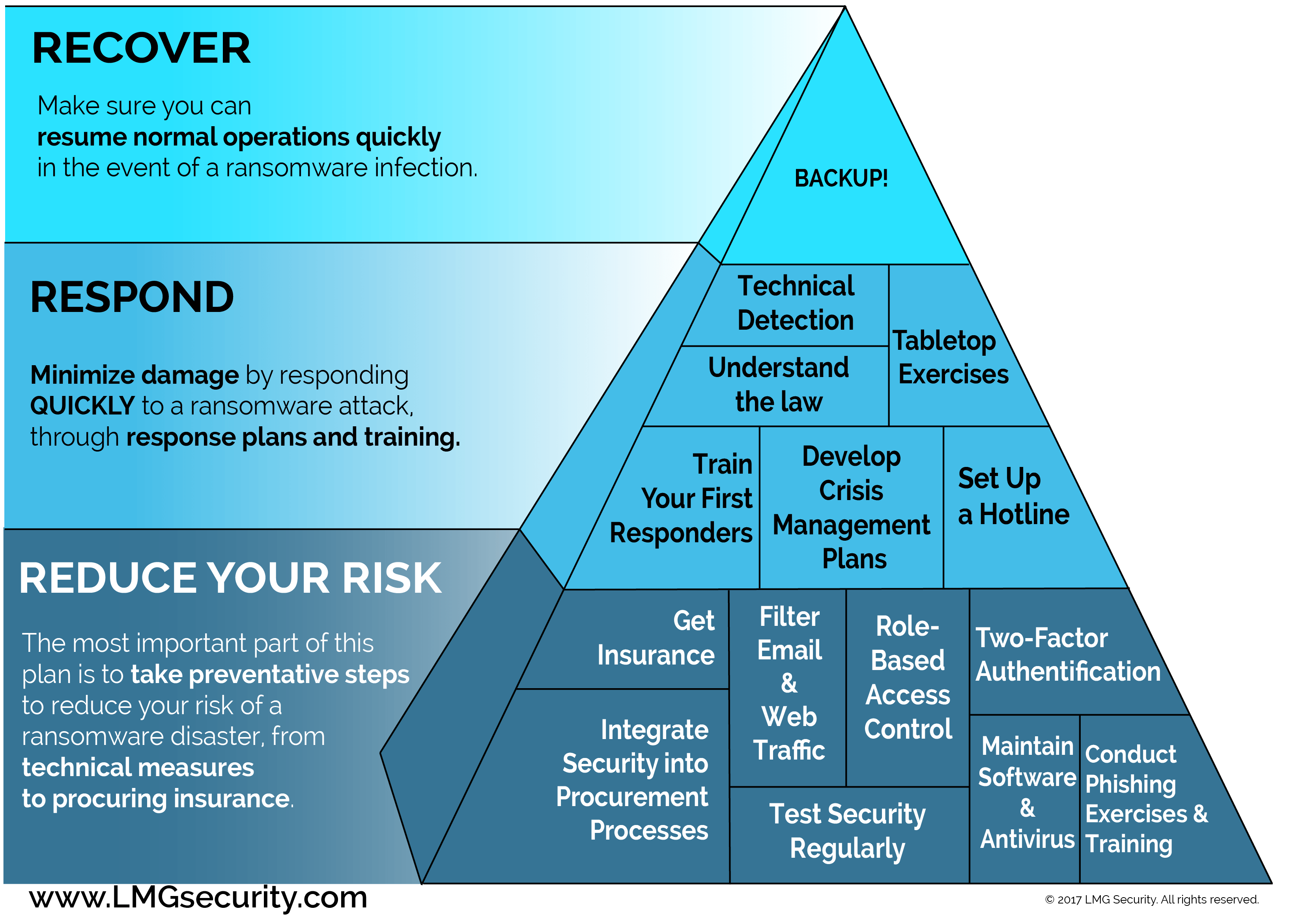
Ransomware is a type of malware from cryptovirology that threatens to publish the victim’s data or perpetually block access. Some more advanced malware uses a technique called cryptoviral extortion which encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them.
