Secure Your Office 365 Accounts

Business Email Compromise (BEC) has become an epidemic in recent years and is now the most common type of data breach that LMG Security encounters. This shouldn’t surprise you. Think about the treasure trove of information contained in your inbox! Social security numbers, passwords, payroll data, tax information, credit card info, and many other types of sensitive data are all commonly found in email accounts. This is a potential goldmine for hackers! A hacked account also opens up any contacts you have to potential phishing attacks that now look legitimate because they’re coming from your account.
The most frightening part of business email compromise isn’t just that it is happening, but how it is happening. Most BEC breaches aren’t due to sophisticated cyber-attacks. Instead, hackers rely on some of the oldest tricks in the book: social engineering and simple deception. Phishing attacks are incredibly common and infuriatingly effective, leading to millions in losses every year due to intellectual property theft and wire transfer fraud. The FBI has reported an increase in business email compromise of over 2000% since 2015. Last year, BEC data breaches were responsible for a staggering $675 million in losses— and those are just the cases that get reported.
Fortunately, all hope is not lost. You can secure your email systems and minimize your risk of compromise. In this post, we’ll walk through important steps you can take to protect your organization, including:
– Enable Multi-factor authentication
Office 365 is by far the most common platform that LMG Security encounters when dealing with Business Email Compromise, so we will use it as an example.
Want to secure your email, fast? Check out LMG Security’s handy open-source Office365 Lockdown Tool, which we’ll discuss in more detail at the end of this post.
Enable Multi Factor Authentication
Passwords alone are not enough to protect your email accounts from today’s cyber threats. Criminals routinely steal passwords using phishing attacks, or purchase passwords on the dark web which were exposed in previous data breaches. You need to add a second method of authentication to protect your organization.
The good news is that Office 365, and many other email providers, include built-in support for multi-factor authentication. Note that SMS (text message) based authentication is no longer considered secure, so it’s best to use a mobile app instead. At LMG we strongly urge all of our clients to enable this feature as soon as possible. Run, don’t walk!
Limit External Forwarding
Often criminals set up mail forwarding and automatic deletion rules as soon as they get access to your account. It is common for criminals to automatically forward or delete messages containing specific terms like “transfer”, “invoice”, or “payment” to an external email account that is owned by the attacker. Occasionally we see the attacker skip the specific words and just forward everything that comes into the account. You could have your email forwarded for six months or more, and not even know it!
LMG Security’s forensics team frequently finds a corresponding rule that marks certain forwarded items as read and sends them to the deleted items folder, so that the legitimate user of the account never sees the affected email in the first place.

You can set up notifications that alert administrators when a new inbox rule is created. Office 365 allows admins to easily create this type of alert, which can help to quickly identify any inboxes that are automatically set to send potentially sensitive information out of the network.
Better yet – if your organization does not have an immediate need for automatic external forwarding, then you can simply remove the ability for users to forward messages to an outside mailbox. This can also reduce your risk of a data breach due to policy violation. This feature can be re-enabled on a per-user basis if one of your users have a legitimate need to do this.
Minimize Access Methods
Criminals often access and download data using protocols that are not actually used by your organization’s legitimate email users. For example, a criminal might initially gain access to an account through the OWA web portal, and then connect via IMAP and download the user’s entire mailbox. All of the data contained in the mailbox is now gone and the attacker can sort through it at their leisure without needing any further connection to the network—leaving you with a huge data breach.
By default, Office 365 allows access via POP3, IMAP, MAPI, EWS, OWA, and ActiveSync for every system user. However, users rarely need access using all of these methods. Does your organization use POP3 or IMAP for email connections regularly? If not – disable them.
There is no point in leaving the doors to your email system wide open if you don’t have to. Disable access methods that employees do not normally use. If a specific user has a legitimate need for access via one of these protocols, you can turn it on it for just that user.
Turn On Audit Logging Right Away
Logs are absolutely critical when assessing a data breach. What did the criminal access? What didn’t they access? In some cases, you need logs to rule out a data breach—but if the logs don’t exist, then you have to assume a criminal accessed everything.
Good news: Office 365 can provide an enormous amount of information that can be very useful in narrowing down the scope of a data breach. Bad news: audit logging is not enabled by default in Office 365 (at the time this was written), and you can’t enable it retroactively. If you need to investigate suspicious activity, you must have already enabled audit logging to have easy access to log data.
All too often, audit logging is not enabled until after a breach was detected, meaning that data leading up to the breach is not available. Audit logs can also be very useful in spotting potential threats before they can actually affect your network. Is an attacker trying to brute-force or password-spray their way into your network? Audit logs can show you that and much more.
There are two ways to accomplish this: One through the portal and one using PowerShell. Follow these steps to enable audit logging through the Office 365 portal:
1. Log in to the Office 365 portal as a properly permissioned administrator. You do not need to be a global administrator to do this, but you will need to be assigned the “Audit Logs” role in Exchange Online
2. Navigate to Search & Investigation => Audit log search. If you don’t see this option, then your permissions are not set correctly or have not taken effect yet. There is occasionally a delay in permission application.
3. Click the link as shown below to enable logging
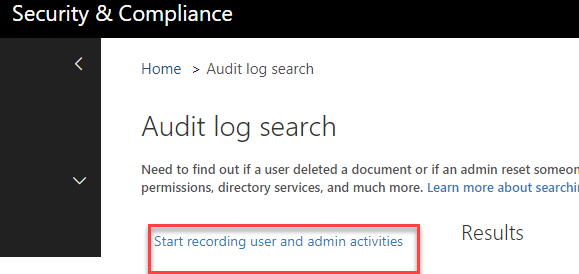
Importantly, enabling audit logging does not enable collection of all recordable events. If you want to track mailbox logins, and record when items are created, copied, moved, deleted, and more, you need to turn on Mailbox Auditing. Mailbox auditing is a separate feature and needs to be enabled independently of the standard audit logs.
More information about data that is collected in Mailbox Auditing can be found here: https://support.office.com/en-us/article/enable-mailbox-auditing-in-office-365-aaca8987-5b62-458b-9882-c28476a66918#ID0EABAAA=Mailbox_auditing_actions
Make sure to set your log retention time. In Office365, the normal retention time is 90 days. That means logs are automatically deleted after 90 days. LMG Security’s team recommends that most organizations retain logs for at least one year. Evaluate your organization’s needs and obligations, and set your log retention time accordingly.
Leverage Scripts
The Office 365 graphical interface is very useful and can be used to complete a large number of tasks, but it is not the most efficient approach to securing Office 365. Common tasks like creating and deleting users, retrieving logs, auditing mailbox contents, and resetting passwords can all be easily scripted, and will help your administrators conduct these tasks more efficiently and consistently.
For example, consider a user who has reported that a phishing email slipped through your filters and is now spreading through your network. Using a script, your admin can simply find the email in the Content Search interface, name the search “Remove phishing email”, then run the following command in PowerShell:
New-ComplianceSearchAction -SearchName "Remove phishing email" -Purge -PurgeType SoftDelete
Having useful little pieces of code like this stashed away in a text file can make retrieval and use fast. This is critical, because when an incident occurs you don’t want your responders wasting time on Google searching for the proper command syntax. Here is a good place to get started: https://docs.microsoft.com/en-us/office365/enterprise/powershell/manage-office-365-with-office-365-powershell
Utilize Secure Score
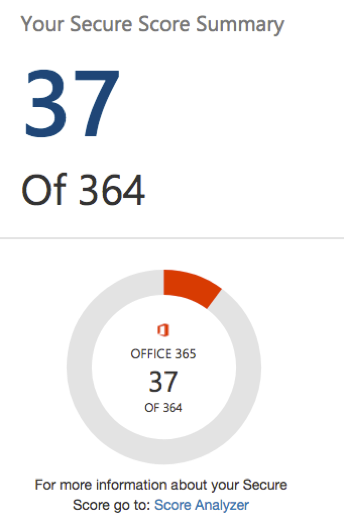
Microsoft provides a built-in analytics tool called “Secure Score” that can show you exactly how at-risk your organization is and what you can do to improve its health. Log on to https://securescore.office.com with an administrator account to see your overall score. The screenshot below shows an example of the Secure Score output (for a test account).
The Secure Score tool also provides your with “Actions” that you can take to improve your score. For example, the following screenshot shows a typical list:
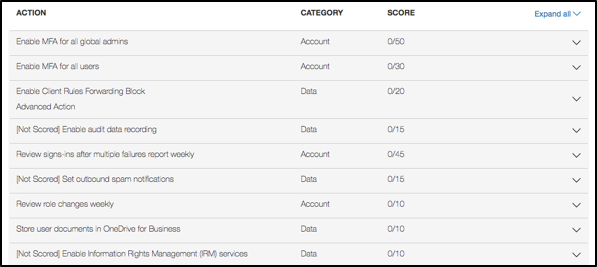
Follow the Actions to enhance your security and increase your score. Steps like enabling multi-factor authentication and audit logging are easy ways to quickly boost your score.
Educate Users
It’s unfortunate, but not all problems related to Office 365 security have a technological solution. Proper user education should always be your first line of defense against account compromise. Train your users to pick strong passwords, recognize the signs of a phishing email, and avoid risky behavior online.
The potential for a breach due to email compromise is present at all levels of an organization. Your training program must include everyone with access to the email system, from the intern working in the copy room to your CEO.
Use Our Handy Office365 Lockdown Script
All of the administrative changes discussed so far can seem like large task for your IT admin to handle, but LMG Security is here to help with that. Our research and development team created a handy Office365 Lockdown script that your IT administrators can use to better secure an Office 365 environment and enable audit logging.
The Office365 Lockdown script will enable full audit logging for your organization, plus give you options to disable access methods and remove forwarding.
You can download the script here:
https://github.com/LMGsec/O365-Lockdown
Feel free to use and modify the script in any way that benefits your organization. (Make sure to read through the README.md file carefully before running the tool.)
Conclusion
There is no “magic bullet” when it comes to protecting your organization’s email accounts. You can dramatically reduce your risk through a combination of technical countermeasures and user training. We hope the Office365 Lockdown tool is helpful for you.
LMG Security can also help you to secure your Microsoft Office 365 environment with our configuration review service. Click here for more information and to request a quote today:
https://www.lmgsecurity.com/o365-review/
Let us know if you have any questions, and follow us on Twitter for more updates!

