The Insider’s Guide to the Rise of Infostealer Malware, Password Spraying, Brute Force, and Credential Stuffing Attacks

Credential theft and authentication attacks are increasing. Cybercriminals are leveraging infostealer malware to harvest user credentials and authentication attacks such as password spraying, brute force attacks, and credential stuffing to break into accounts and networks. These methods exploit common security weaknesses and human behavior to gain unauthorized access to sensitive systems. Let’s dive into the technical differences and then we’ll share a few resources to reduce your risk.
Infostealer Malware
The Snowflake data breach in 2024 highlighted the risks posed by infostealer malware and stolen passwords. Last month, the two men who led the group that allegedly compromised multiple organizations’ Snowflake-hosted cloud environments to extort $2.5 million from at least three victims, and breach many others, were indicted. The cybercrime group exploited credentials stolen using infostealer malware to access the online environments of 165 organizations and attempted to extort at least 10 organizations after stealing billions of sensitive customer records. The majority of affected Snowflake accounts either lacked multi-factor authentication (MFA) or had inadequate network access restrictions, making it easier for attackers to obtain sensitive customer data. Despite Snowflake’s core systems remaining secure, the failure of some customers to enforce stronger access controls exposed them to significant risk.
The damages from this infostealer malware breach were widespread, affecting over 165 Snowflake customers, including major companies such as AT&T, Santander Bank, and Ticketmaster. Stolen data was exfiltrated and, in some cases, used for extortion, as attackers demanded ransoms for its return. The breach caused operational disruptions, reputational damage, and financial losses for victims. Snowflake has since implemented mandatory MFA and introduced stricter security measures for customer accounts, but this incident underscores the critical need for robust defenses against credential theft.
Now that we’ve covered the implications of infostealer malware, let’s dive into popular authentication attacks, including brute-force, credential stuffing, and password spraying attacks.
Popular Authentication Attacks
Authentication attacks come in different variations with some distinct nuances. Most folks are at least familiar with the term “brute-force attacks.” But, are you aware of the differences between a brute-force attack and password spraying? Or credential stuffing? We’ll explain some of the key differences between various authentication attack types.
Brute-Force
Let’s start with brute-force attacks. Brute-force is defined by Merriam-Webster as “relying on or achieved through the application of force, effort, or power in usually large amounts instead of more efficient, carefully planned, or precisely directed methods.” In this sense, brute-force authentication attacks can be thought of as an attack that employs overwhelming force to determine valid credentials. Typically, brute-force attacks will target a single account identifier (username, email address, etc.) with large lists of possible passwords, attempting each in succession until the correct password is determined, the account is locked out, the attack is mitigated, or the threat actor abandons her efforts.
We frequently use brute-force attacks on pentests. First, I create a base wordlist through both manual and automated means with something like CeWL and some open-source intelligence (OSINT). This base wordlist is then mangled with either Hashcat or John the Ripper and some select rule sets. The process of mangling involves creating variations of the words in the wordlist that include commonly used “complexity”, such as capitalizing the first letter, adding “!” to the end, or appending 1 or the current year “2024”.
There are lots of tools that come in handy when performing authentication attacks, including:
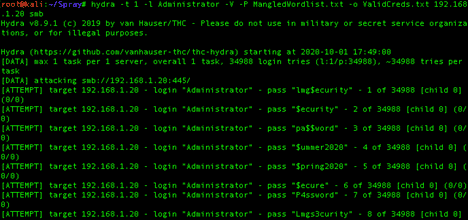
This list is by no means exhaustive. Each of these tools has its place, and many can be used for multiple purposes. That said, my favorite tool for brute-forcing network services is Hydra. The following screenshot shows Hydra using a custom wordlist to brute-force attack the “Administrator” user on the host 192.168.1.20 in an attempt to correctly guess the user’s password.
Credential Stuffing
Credential stuffing is another form that authentication attacks may take. In credential stuffing, valid credentials for one service are used to attempt to authenticate to other services. Unfortunately, password reuse is still extremely common and compromised account credentials are constantly being bought and sold online by threat actors. Often these compromised credentials will be leveraged to authenticate to additional services, applications, or systems. Collections of compromised credentials, known as “dumps,” are publicly available if you know where to look. These dumps are frequently used by threat actors to attempt to compromise additional accounts belonging to the affected user. For example, a set of compromised credentials may be used to attempt to authenticate to that same user’s email, bank(s), social media accounts, or even their employer’s network! Utilizing Multi-Factor Authentication (MFA), along with lengthy, unique, passwords for every account and a password manager to organize them can go a long way in mitigating credential stuffing attacks. Check out LMG’s recommended password practices in a great post written by my colleague, Ben Kast.
Credential stuffing can be effective on pentests, though I don’t use it as frequently as brute-forcing or password spraying. There have been countless times during pentests where I’ve stumbled upon credentials stored in a text file, word doc, spreadsheet, you name it, with no indication of where or what they may be used for. This is where credential stuffing comes in!
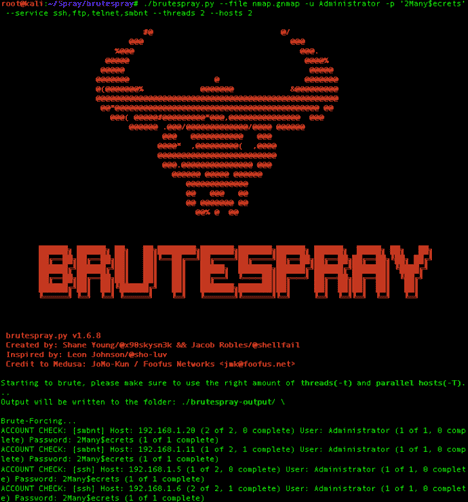
I’ve found BruteSpray to be an effective tool for credential stuffing attacks, though there are certainly others. The following screenshot shows BruteSpray utilizing the username “Administrator” and password “2Many$ecrets” to attempt to authenticate to the SSH, FTP, Telnet, and SMB services across the hosts contained in an Nmap .gnmap output file.
Password Spraying
Password spraying is yet a third variation of an authentication attack. This form of authentication attack employs lists of usernames and then pairs these with common passwords. Password spraying attacks are generally less focused than brute-force attacks. The focus of a brute-force attack is usually an account, or a handful of known accounts, which are then subjected to large lists of possible passwords. Password spraying flips this around a bit—common, or default, passwords are used against a large list of possible usernames. So, where the many-to-one ratio in brute-force attacks is many passwords to one username, in password spraying it is many usernames to one password. This is a conceptually different way of performing authentication attacks as the “known variable” is the password, not the account name. Whereas in a brute-force attack, the known variable is the username. Real-world password spraying attacks will incorporate lists of common, default, or known passwords.
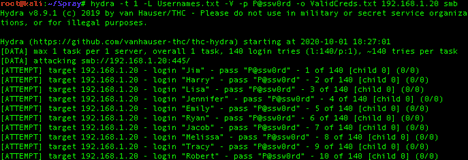
I find that one of the most valuable pieces of information when conducting internal penetration tests is the list of all of the usernames in the organization’s domain. Once I have that I will start password spraying using some really common passwords like “Summer2020” or “P@ssw0rd”. Hydra again is my go-to tool for this. The following screenshot shows the password “P@ssw0rd” being “sprayed” across multiple different user accounts.
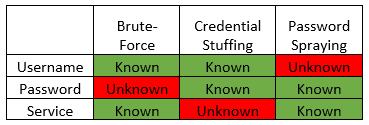
The following table provides a simplified breakdown of these three authentication attack types, including which variables are known, as well as which are unknown (being targeted).
Services supporting authentication are prime targets for threat actors as much of the time valid credentials are the only barrier preventing access to sensitive systems, applications, or data. Blue teams can help mitigate these attacks by limiting the attack surface through the use of ACLs, network segmentation, strong password practices, MFA, and account lockout policies.
How Can You Reduce Your Risk?
To reduce your risk from infostealer malware and authentication attacks such as password spraying, brute force attacks, and credential stuffing, follow these best practices:
- Implement Multi-Factor Authentication (MFA): Add an extra layer of security to prevent unauthorized access even if credentials are stolen. Read our MFA blog for more details.
- Create Policies that Require Strong, Unique Passwords or Passwordless Authentication: Ensure passwords are complex, include a mix of characters, and avoid reuse across accounts. Read our blogs on passwordless authentication and password length guidelines for more actionable tips.
- Deploy Endpoint Protection Solutions: Use advanced tools to detect and block infostealer malware on devices.
- Educate Employees: Train staff on recognizing phishing attempts and avoiding malware downloads. Read our tips on how to turn your employees into a human firewall.
- Restrict Access with Identity and Access Management or Zero-Trust Architecture: Minimize the risk of unauthorized entry by limiting access based on roles and verifying every login attempt.
- Implement Rate-Limiting and Lockouts: Protect against brute force and credential stuffing by limiting repeated login attempts.
- Leverage Behavioral Analytics: Use tools to monitor unusual access patterns and flag suspicious activity.
We hope this information on credential theft, infostealer malware, and authentication attacks has been helpful. Please contact us if you need help with technical testing, advisory or compliance services, or technical training.

