Top Takeaways from the 2020 Verizon Data Breach Investigations Report

As a contributing organization, LMG Security had a sneak peek at the findings. Hot off the presses, here are the top takeaways from this year’s Verizon Data Breach Investigations Report:
- Errors are up! The only type of threat action that has increased slowly and steadily over the years, this category includes misconfiguration, misdelivery, publishing errors and more. With organizations steadily uploading ever-increasing volumes of data to the cloud, it’s no surprise that more errors lead to data breaches. All it takes is one system administrator to accidentally set a data repository to be public, and your organization could be the next headline. The spike in “misconfiguration” issues since the start of 2018 is telling; around this time frame, security researchers became adept in scanning for misconfigured AWS buckets and similar caches of exposed data.
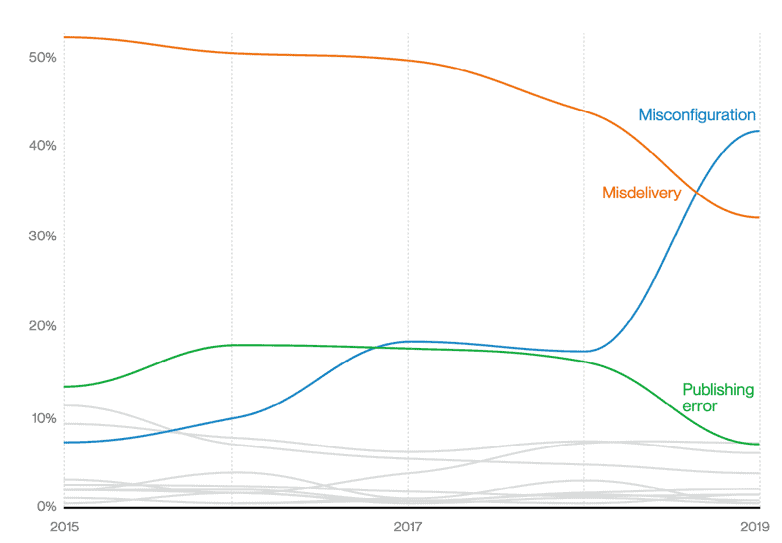
Figure 1: “Top error varieties over time in breaches” – 2020 Verizon Data Breach Investigations Report
- Passwords are our biggest weakness. The two top threat actions this year were (again) phishing and use of stolen credentials. But drilling down, over 60% of phishing breaches resulted in—you guessed it—compromised credentials. In other words, the majority of phishing attacks led to stolen passwords, which in turn enabled criminals to hack into networks. Similarly, when victims were infected with malware, the top variety was a password dumper (nearly 40% of breaches involving malware). “Hackers don’t break in, they log in,” said Microsoft executive Bret Arsenault. Two-factor authentication is critical for reducing every organization’s risk—although not all two-factor authentication methods are equally effective.
- Half of all data breaches were reported by an external security researcher, and another third were reported by customers or other third parties. Of course, when data breaches are discovered by a third party, they may be more likely to be publicly reported: “the victims have no choice but to utter ‘mea culpa.’” If only there were a way to track unreported data breaches, too!
- Organized crime groups were the perpetrators in over half of data breaches, while nation-state actors were behind approximately 10% of cases. This was roughly in line with reports from rival cybersecurity company CrowdStrike, which reported in mid-2019 that “eCrime” activity (financially motivated cyberattacks) were up at the expense of nation-state attacks. In addition to the findings in the 2020 Verizon Data Breach Investigations Report, LMG Security’s incident response team has observed the shifting trend towards organized crime firsthand. There is now a steady stream of business email compromise and ransomware cases which have all of the hallmarks of organized criminal gangs out to make a profit.
- System administrators and end-users were the perpetrators of nearly 20% of all data breaches—although not (presumably) on purpose! This circles back to the prevalence of errors as a cause of data breaches this year; humans are your first line of defense, after all, and when one person—even a normal end user—makes a mistake, it can have serious consequences.
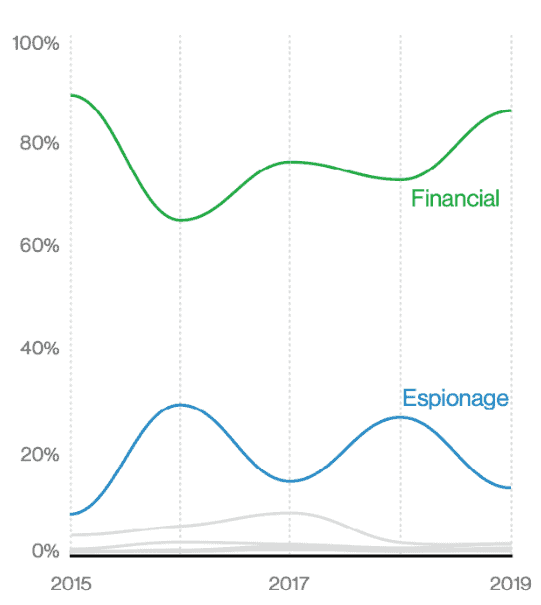
Figure 2: “Actor motives over time in breaches.” from the 2020 Verizon Data Breach Investigations Report.
- Criminals are financially motivated in over 80% of data breaches, up from last year. Espionage was a distant second, making up less than 20% of this year’s breaches.
- Ransomware is increasingly showing up in reported data breach cases. Investigators for the 2020 Verizon Data Breach Investigations Report determine that the criminals steal passwords and compromise confidential data prior to encrypting it. The recent trend of exposure extortion (perpetuated by Maze and REevil, among other groups) will only increase the number of ransomware cases that are also declared data breaches. Restoring a victim’s data and resuming operations is challenging enough; more and more often, victims must juggle those activities with preserving evidence and launching a data breach investigation.
To protect yourself and your organization against today’s top threats, remember:
- Use Two-factor Authentication whenever possible.
- Think Before You Click. Don’t fall for scams or phishing emails. Train every member of your organization on safe cybersecurity practices.
- Check Your Cloud Configuration. Make sure you minimize your exposure interfaces and configure your cloud repositories properly.
The 2020 Verizon Data Breach Investigations Report reflects a changing world, where data is increasingly stored in the cloud, and savvy organized crime groups have developed sophisticated tactics for monetizing their cyberattacks. Recently, the transition to remote work and an accelerated rush to the cloud has only left more login interfaces vulnerable and a doubtless trail of misconfigured data repositories exposed to the Internet. These changes will only accentuate existing trends: the prevalence of password-based attacks, errors that lead to data breaches, and financially driven organized crime actors. Cybersecurity teams must stay vigilant, continuously updating and re-evaluating their policies, procedures, and services. Organizations should strive to combine best cybersecurity practices, strong hardware/software, user training, proactive security programs, and ongoing security gap testing to ensure a strong security posture.
Many thanks to LMG Security’s excellent incident response team for analyzing and submitting their data breaches and cybersecurity incidents for inclusion in the 2020 Verizon Data Breach Investigations Report. Special credit to Karen Sprenger, Matt Durrin, Ari Apedaile, Sam Wolf Delaney Moore, Shalena Miller, Peter Arant, and Parker Lee for their work. Stay safe, everyone!

