Watch Ransomware Wreak Havoc in the Cloud
What does it actually look like when ransomware encrypts all the files on an employee workstation… and then moves on to encrypt your company’s file share, and even cloud-based documents? Today LMG Security released a video which shows an unsuspecting employee, “Dan D,” clicking on a link and getting infected with the “Jigsaw” ransomware. Watch as “Jigsaw” holds the fictitious company HackMe, Inc for ransom and starts the countdown clock. Narrated by LMG Senior Consultant Dan Featherman, the video is an excellent way to show your friends and colleagues how ransomware works, and what NOT to do.
Ransomware has become a critical issue, shutting down hospitals and causing major headaches for many organizations. Many enterprises are pushing files to the cloud, hoping that moving files offsite is a solution, but as you can see in this video, ransomware can often spread not only to networked file shares, but also cloud-based systems such as OneDrive.
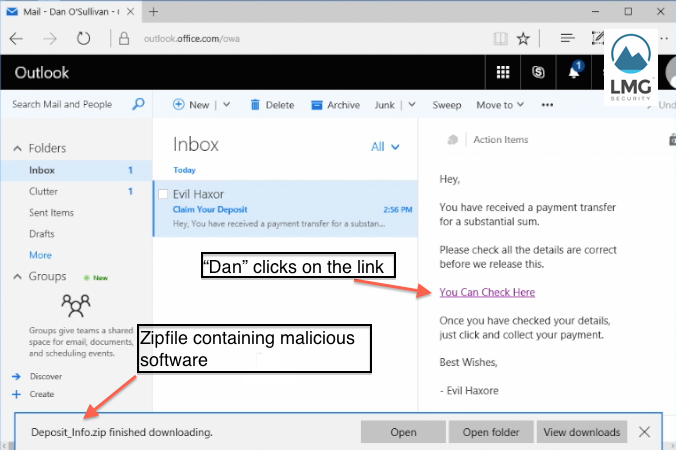
The video was created in LMG’s “Play Lab,” an isolated environment for Network Forensics research. Below are a few snapshots from the video, in which employee “Dan D” clicks on a link in a phishing email from “Evil Haxor”:
As soon as he clicks, the zipfile downloads automatically. Next, “Dan” extracts and opens the Deposits file, thinking that it’s a legitimate document. The ransomware installs itself and produces a pop-up with a registration message and confirmation code.
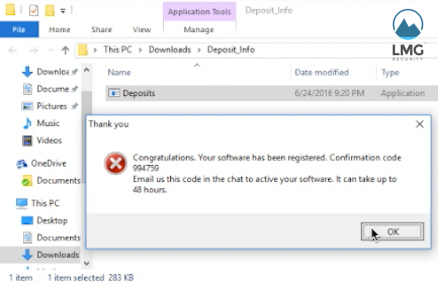
Once installed, the Jigsaw Ransomware pops up a registration message with a “confirmation code.
Slowly, the files on the desktop start to change, as Jigsaw locks them up one by one:
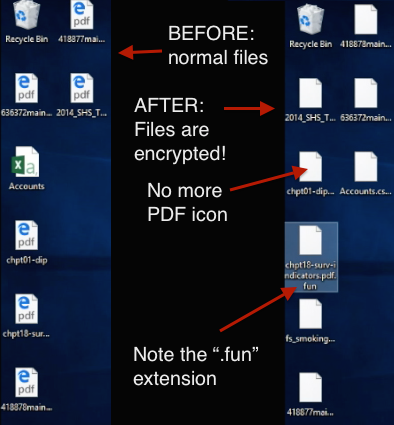
“Jigsaw” locks up files on the desktop.
The Jigsaw ransomware then goes on to lock up the company’s network file share (the Y drive)!
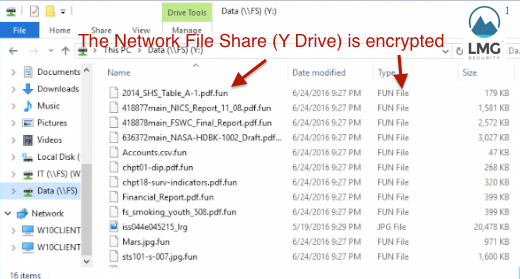
Jigsaw encrypts files in the network storage folder (Y drive).
… and even locks up the cloud file repository, hosted in OneDrive.
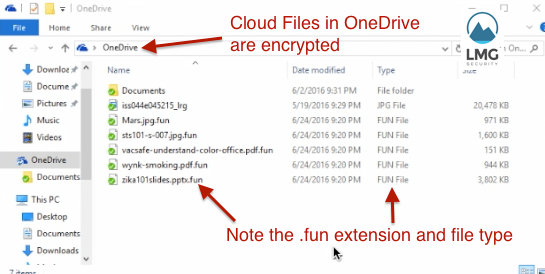
Even cloud-based files in OneDrive are encrypted.
Suddenly, a ransom note pops up! “You have 24 hours to pay 150 USD in Bitcoins to get the decryption key.”
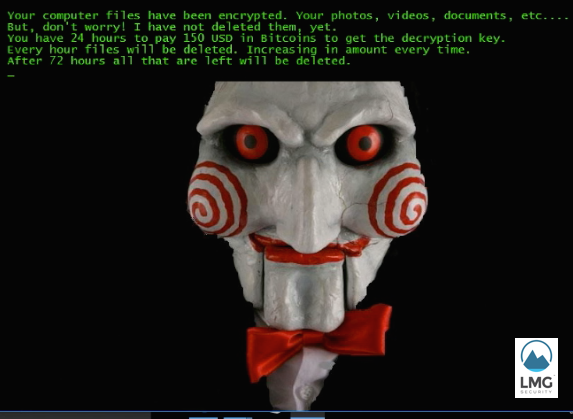
A ransom note pops up!
A countdown timer starts, at 60 hours:
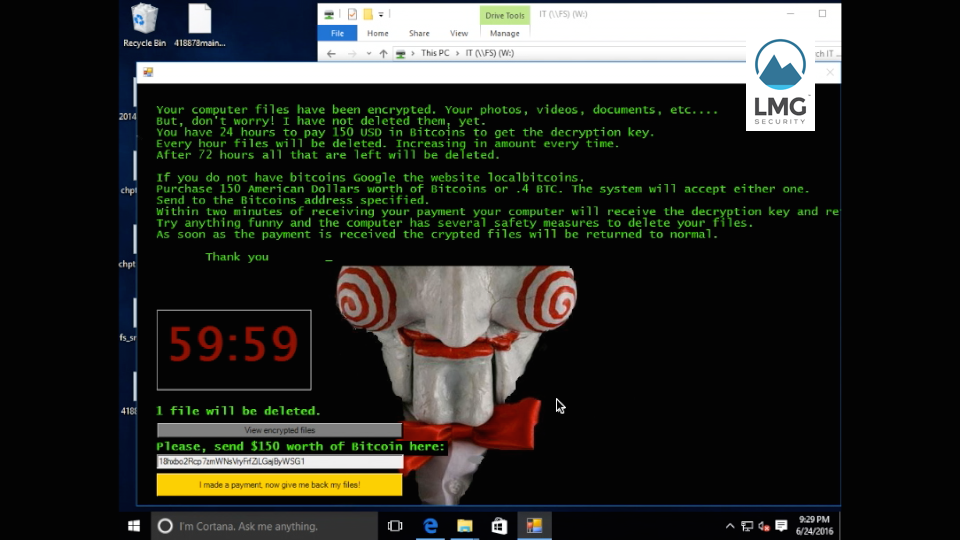
A countdown timer starts.
“Every hour files will be deleted,” says the ransom note. “After 72 hours all that is left will be deleted.”
Here’s a screenshot showing files on the network share that have been deleted, according to Jigsaw:
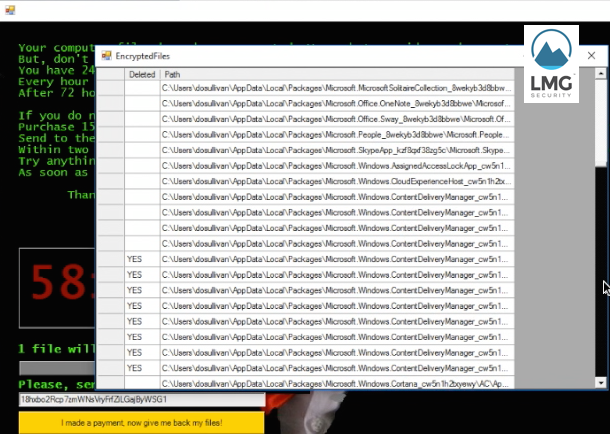
“Every hour files will be deleted.”
Join us in the Network Forensics class at Black Hat, July 30-Aug 2, where we’ll release the full packet captures of the Jigsaw ransomware infection! Also, stay tuned for updates and more videos soon.