Why Continuous Attack Surface Monitoring Should Be A 2024 Cybersecurity Goal
 Long gone are the days when a monthly vulnerability scan could deliver peace of mind. The recent attack on Change Healthcare, which disrupted prescription processing services for over 67,000 pharmacies and 129 million individuals, was linked to the exploitation of a new vulnerability merely days after the vendor published a patch. Software exploits served as the initial intrusion point for 32% of attacks, according to Mandiant, and certified software vulnerabilities grew another 15% in 2023, with over 29,000 CVEs. In this article, we’ll discuss the importance of continuous attack surface monitoring (including finding the unknown, shadow IT attack surfaces), how to protect yourself from software vulnerabilities, and how continuous attack surface monitoring tools can reduce your risk of a breach.
Long gone are the days when a monthly vulnerability scan could deliver peace of mind. The recent attack on Change Healthcare, which disrupted prescription processing services for over 67,000 pharmacies and 129 million individuals, was linked to the exploitation of a new vulnerability merely days after the vendor published a patch. Software exploits served as the initial intrusion point for 32% of attacks, according to Mandiant, and certified software vulnerabilities grew another 15% in 2023, with over 29,000 CVEs. In this article, we’ll discuss the importance of continuous attack surface monitoring (including finding the unknown, shadow IT attack surfaces), how to protect yourself from software vulnerabilities, and how continuous attack surface monitoring tools can reduce your risk of a breach.
What Is Your Organization’s Attack Surface?
Your attack surface includes anything an attacker can use to access your environment, data, or operations. “There is no perimeter anymore,” says Tom Pohl, LMG’s penetration testing team lead. With the prevalence of SaaS and public clouds, our pentest team often finds initial entry points resulting from connected supplier software, exposed legacy systems, cloud misconfigurations, and more. In addition, systems have become increasingly interconnected, and we are seeing a rise in “shadow” attack surfaces—where departments add a new cloud provider or partner integration without talking to IT. This is where the concept of continuous attack surface monitoring comes into play. The right continuous attack surface monitoring solution can automate rapid asset detection, in addition to helping you discover new vulnerabilities.
How to Identify Your Entire Attack Surface
Identifying your attack surface is an ongoing process that often evolves over time. If you’re working with a very small budget and looking for a quick, free view, you can try Shodan—a search engine that can help you discover exposed attack surfaces. It can show you hardware, software versions, open services, and vulnerable devices with open ports; it can be a valuable source of open-source intelligence gathering (OSINT) for mapping your systems.
OSINT should also serve as part of a comprehensive attack surface management plan. You can use many free or low-cost OSINT tools to collect information to help identify your attack surface. As you consider defending your system, remember that hackers can also use these publicly available tools to gather information, as well as discover the names of employees and services used by your organization. They can then use this data for customized phishing attacks and password spraying attacks.
For a more full-featured approach, we recommend using a continuous attack surface monitoring tool to monitor your attack surface and manage your software vulnerabilities in an integrated platform. While we use Tenable One internally and recommend it to our clients, there are certainly many options. A continuous attack surface monitoring tool helps you determine your attack surface, monitor it, identify exposure, manage vulnerabilities, inventory assets, and prioritize your remediation efforts. Here’s a screenshot of our team using the Tenable continuous attack surface monitoring tool to map assets.
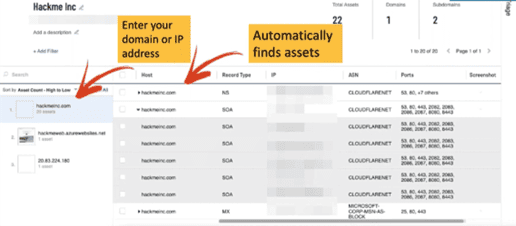
Screenshot of using Tenable One for asset mapping.
How Continuous Attack Surface Monitoring Tools Reduce Your Risk from Software Vulnerabilities
Many software vulnerabilities don’t show up on vulnerability scans—especially zero-day weaknesses or newer vulnerabilities that have not yet had time for proper integration into scanning utilities. Attack surface monitoring is key to reducing risk because it enables defenders to identify and then minimize services that are exposed to the Internet.
Continuous attack surface monitoring tools may also include built-in version identification and vulnerability scanning features. This can enable you to identify unpatched systems and confirm when a patch has been applied. It provides comprehensive reporting and will give you a rating for the vulnerabilities to help you track, manage, and prioritize remediation. We recommend that you schedule daily scans and review them to create prioritized remediation plans. Here’s a sample of the prioritized dashboard.
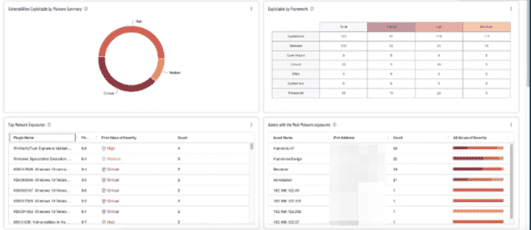
Screenshot of the Tenable One dashboard for our sample company, Hackme, Inc.
Some continuous attack surface monitoring tools can also provide attack mapping pathways that show what types of services can be accessed and attacked using the vulnerability. This can provide your team with guidance as you assess potentially connected services and create a plan to prioritize and remediate these vulnerabilities.
A Checklist for Implementing an Effective Vulnerability Management Program
Using a continuous attack surface monitoring tool is a great start for creating an effective vulnerability management program, but it is only part of the solution. You also need to:
- Establish a formal vulnerability management program with documented policies and procedures. It can be as simple as using the prioritized list from your continuous attack surface monitoring tool and defining a process for tracking the assignment and remediation status of these vulnerabilities. Check out our blog on 6 patch management mistakes to avoid and reach out if you need help creating cybersecurity policies and procedures; our advisory services team can help.
- Maintain an accurate data and asset inventory. If you don’t know what you have, you can’t protect it. It can take up to 120 days for vulnerabilities to be incorporated into your vulnerability scanning software, and an asset inventory is critical to quickly see if you’re running vulnerable software, where it’s located, and the systems to which it is connected. You also need to know if the software is connected to other critical systems that would need to be taken down for a day when you remediate the vulnerability. You should map your network infrastructure and understand essential connections such as internal subnets, VLANS, access points, and external connectivity. You should also map your data, location (on-premises or cloud), encryption status, and accessibility.
- Scan for vulnerabilities at least daily; continuous scanning is preferred, if possible.
- Prioritize your remediation activities by highest risk. You can use the continuous vulnerability monitoring tool’s list or make your own.
- Patch quickly. Some continuous vulnerability management tools even have automated patching and patch confirmation that delivers efficient patching that further decreases your risk.
- Conduct regular human-led penetration tests. Most breaches result from a hacker gaining a foothold, and then using that to move laterally and gain greater access and information. Vulnerability scanning is a critical foundation, but it cannot chain together vulnerabilities, find and exploit misconfigurations, and move laterally like a skilled human pentester will. Penetration testing simulates how attackers break into your systems and catches many security gaps that vulnerability scanners miss, like printer vulnerabilities that can be leveraged for full system takeovers, SaaS vulnerabilities that can compromise ALL SaaS user accounts (read our blog for a detailed look at how our pentest team found a vulnerability that provided super-admin access to all the vendor’s client accounts), and more. You should also include your cloud environments and third-party software in your pentests for a more accurate assessment of your risks.
- Implement supplier security policies. Contractually require suppliers that are connected to your environment or hold your data to conduct regular pentesting. For more information on reducing your cybersecurity risks from suppliers, read our supply chain security blog.
- Include plans for software vulnerability breaches in your incident response plan. Read more about this topic in our recent blog that explains how to run software vulnerability incident response tabletop exercises that help prepare your team for a breach.
We hope you found this guide helpful. Please contact us if you have any questions or would like support with implementing a continuous vulnerability monitoring tool, pentesting, policy development, training, and more. Our expert team is ready to help!
