New Tool Makes Office 365 Attack Testing More Efficient
During a recent red ream engagement, I obtained quite a few email addresses for the target organization to use in brute-force password-guessing attacks. Office 365 is susceptible to user enumeration techniques that allow malicious actors to determine whether or not a particular email account is valid; a “feature” that is deemed a non-issue by Microsoft. However, smart hackers can leverage user enumeration to conduct an Office 365 attack to gain the credentials to breach your network.
What is User Enumeration?
User enumeration is the process of determining whether an account is valid or not. This “trial and error” is used to make brute force password guessing attacks more efficient. This happens before the actual brute-force attack occurs and can make an Office 365 attack more efficient.
How do Hackers Leverage User Enumeration in an Office 365 Attack?
User enumeration can aid attackers in creating efficient target lists to use in subsequent attacks. Most of these techniques require performing an authentication attempt (using a password) to determine if the account is valid, which is simple to automate but counts towards the lockout threshold set in the organization’s password policy. While manually validating some accounts through the Office 365 web portal, I noticed that valid and invalid accounts produced different responses from the server before even entering a password, so I decided to take a deeper look…
Enumerating Valid Office 365 Accounts
I found that the Office 365 web portal will behave one of two ways when entering an email address to begin the authentication process:
When a valid email address is submitted to the web portal, the page changes to a password prompt with no errors, as shown below:
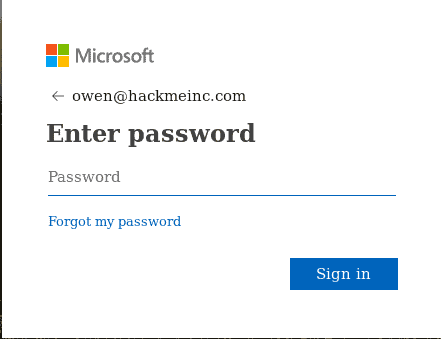
Legitimate User Account Login Page
Conversely, when entering an invalid email address, the page gives an error message and does not advance to the password entry, as shown below:
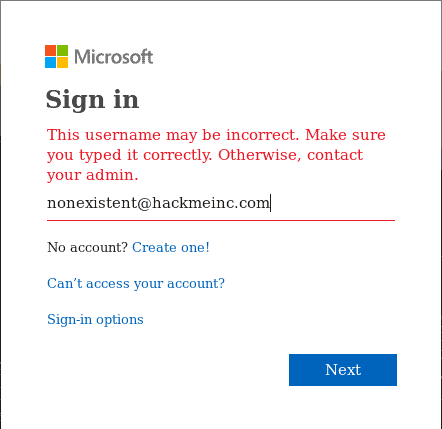
Invalid User Account Login Attempt
I fired up the web application security testing tool, Burp Suite, to look at the web server requests and responses for both valid and invalid email addresses. The partial screenshot below shows that a POST request is sent to the URL “https://login.microsoftonline.com/common/GetCredentialType” with the email address included within the “Username” parameter of the submitted data.
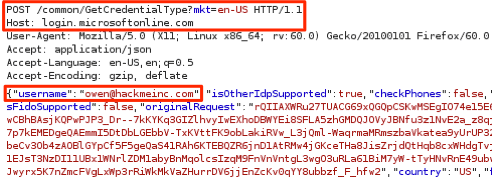
POST Request to Office 365 Server
The server checks if the account is valid and returns a response with the ““IfExistsResult”:0” parameter. In this case, since the account is valid, the parameter is set to 0 as shown below:

Valid User Response from Server
When an invalid address is entered, the server responds with the “IfExistsResult” parameter set to 1:
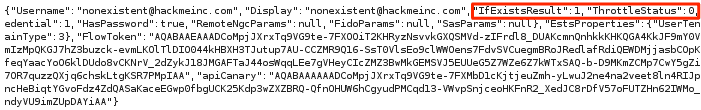
Note the “ThrottleStatus” parameter: In short, Office 365 will “throttle” the responses and give erroneous results (such as false positives) based upon an unknown determining factor. I was only able to produce a false positive that showed an invalid account as valid after multiple repeated attempts in quick succession.
Introducing “o365creeper.py”
There didn’t seem to be any tools that automated this process in the manner I wanted, so I set out to create one. This will be helpful for your, and our, future Office 365 brute force attack tests. The tool, written in Python and named “o365creeper.py”, is available on LMG Security’s GitHub page and basically automates the manual process I showed above. It takes either one email address with the “-e” argument, or a full list of email addresses with the “-f” argument and outputs whether each address is valid or not, all while never submitting an actual login attempt. The “-o” argument makes the script output only the valid email addresses so they can then be put straight into your brute-force password-guessing tool of choice. An example of the usage is shown below.
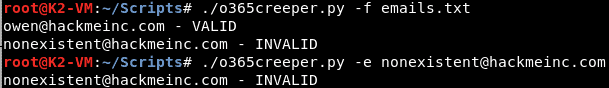
o365creeper Email Address Validation
While this process is not a particularly new discovery or a vulnerability per se, this tool can be used to verify valid and invalid email addresses on client Office 365 tenants without submitting login attempts. This can be useful in red team or penetration testing engagements where you want to make your user lists efficient and stay quiet for as long as possible during an Office 365 brute force attack. Ideal usage of this tool is to use the “-f” argument to feed it a list of gathered email addresses for validation, not to brute-force enumerate email addresses. There are a number of quality posts on the Internet that outline effective ways of using Open-Source Intelligence (OSINT) gathering techniques to find email addresses to use in brute-force password-guessing attacks.
We hope your penetration testing team finds this new tool helpful when conducting an Office 365 brute force attack during red team testing or advanced penetration testing. If you don’t have an internal penetration testing team, our innovative, experienced team conducts highly effective technical testing, so you can sleep at night.
